Question 416
Ann, a security administrator, is conducting an assessment on a new firewall, which was placed at the perimeter of a network containing PII. Ann runs the following commands on a server (10.0.1.19) behind the firewall:

From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:
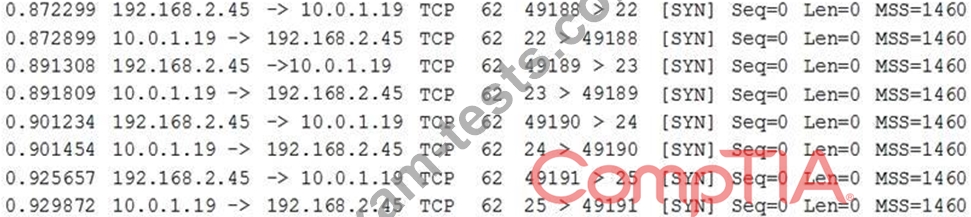
Connectivity to the server from outside the firewall worked as expected prior to executing these commands.
Which of the following can be said about the new firewall?

From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:

Connectivity to the server from outside the firewall worked as expected prior to executing these commands.
Which of the following can be said about the new firewall?
Question 417
A business is growing and starting to branch out into other locations. In anticipation of opening an office in a different country, the Chief Information Security Officer (CISO) and legal team agree they need to meet the following criteria regarding data to open the new office:
Store taxation-related documents for five years

Store customer addresses in an encrypted format

Destroy customer information after one year

Keep data only in the customer's home country

Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
Store taxation-related documents for five years

Store customer addresses in an encrypted format

Destroy customer information after one year

Keep data only in the customer's home country

Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
Question 418
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrate captures an attempted authentication and discovers the following being presented by the user's VPN client:
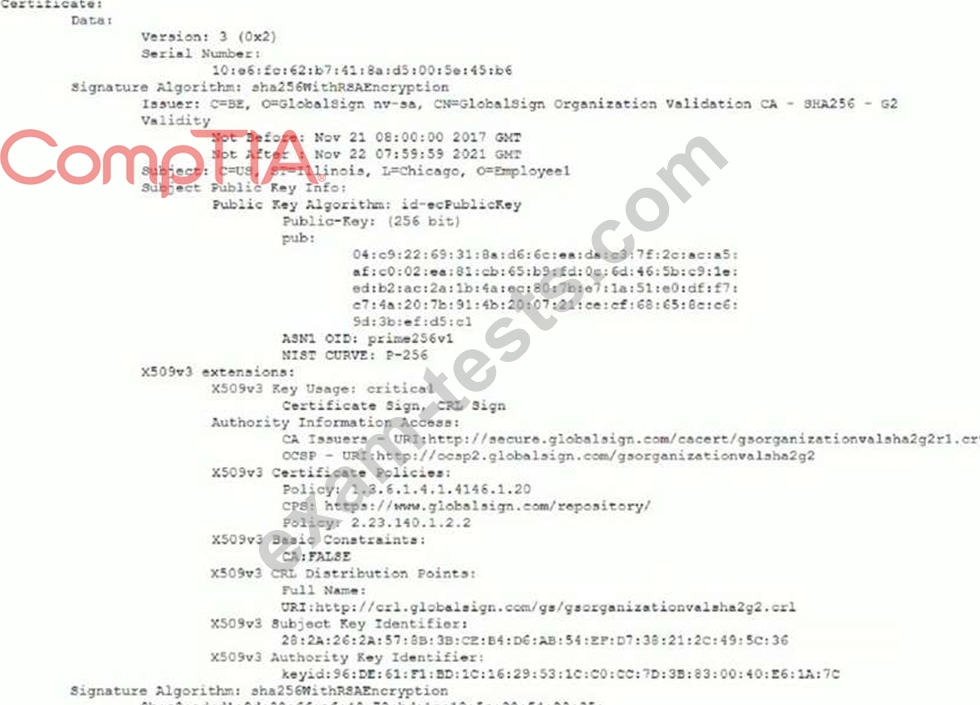
Which of the following BEST describes the reason the user is unable to connect to the VPN service?

Which of the following BEST describes the reason the user is unable to connect to the VPN service?
Question 419
A system administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
Question 420
A university Chief Information Security Officer is analyzing various solutions for a new project involving the upgrade of the network infrastructure within the campus.
The campus has several dorms (two-four person rooms) and administrative buildings.
The network is currently setup to provide only two network ports in each dorm room and ten network ports per classroom.
Only administrative buildings provide 2.4 GHz wireless coverage.
The following three goals must be met after the new implementation:
1. Provide all users (including students in their dorms) connections to the Internet.
2. Provide IT department with the ability to make changes to the
network environment to improve performance.
3. Provide high speed connections wherever possible all throughout
campus including sporting event areas.
Which of the following risk responses would MOST likely be used to reduce the risk of network outages and financial expenditures while still meeting each of the goals stated above?
The campus has several dorms (two-four person rooms) and administrative buildings.
The network is currently setup to provide only two network ports in each dorm room and ten network ports per classroom.
Only administrative buildings provide 2.4 GHz wireless coverage.
The following three goals must be met after the new implementation:
1. Provide all users (including students in their dorms) connections to the Internet.
2. Provide IT department with the ability to make changes to the
network environment to improve performance.
3. Provide high speed connections wherever possible all throughout
campus including sporting event areas.
Which of the following risk responses would MOST likely be used to reduce the risk of network outages and financial expenditures while still meeting each of the goals stated above?

