Question 446
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization's file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system.
Which of the following is MOST likely to be reviewed during the assessment? (Select two.)
Which of the following is MOST likely to be reviewed during the assessment? (Select two.)
Question 447
Following a merger, the number of remote sites for a company has doubled to 52. The company has decided to secure each remote site with an NGFW to provide web filtering, NIDS/NIPS, and network antivirus. The Chief Information Officer (CIO) has requested that the security engineer provide recommendations on sizing for the firewall with the requirements that it be easy to manage and provide capacity for growth.
The tables below provide information on a subset of remote sites and the firewall options:
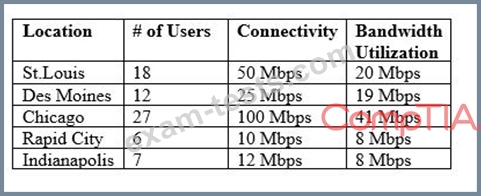
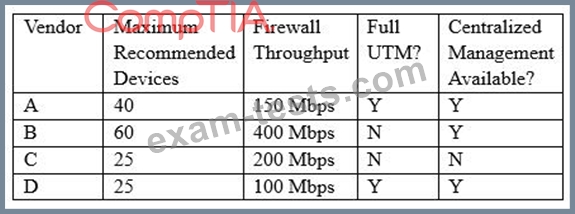
Which of the following would be the BEST option to recommend to the CIO?
The tables below provide information on a subset of remote sites and the firewall options:


Which of the following would be the BEST option to recommend to the CIO?
Question 448
Warehouse users are reporting performance issues at the end of each month when trying to access cloud applications to complete their end of the month financial reports.
They have no problem accessing those applications at the beginning of the month.
Network information:
DMZ network-192.168.5.0/24
VPN network-192.168.1.0/24
Datacenter-192.168.2.0/24
User network-192.168.3.0/24
HR network-192.168.4.0/24
Warehouse network-192.168.6.0/24
Finance network 192.168.7.0/24
Traffic shaper configuration:
VLAN Bandwidth limit (Mbps)
VPN 50
User 175
HR 220
Finance 230
Warehouse 75
Guest 50
External firewall allows all networks to access the Internet.
Internal Firewall Rules:
ActionSourceDestination
Permit 192.168.1.0/24 192.168.2.0/24
Permit 192.168.1.0/24 192.168.3.0/24
Permit 192.168.1.0/24 192.168.5.0/24
Permit 192.168.2.0/24 192.168.1.0/24
Permit 192.168.3.0/24 192.168.1.0/24
Permit 192.168.5.0/24 192.168.1.0/24
Permit 192.168.4.0/24 192.168.7.0/24
Permit 192.168.7.0/24 192.168.4.0/24
Permit 192.168.7.0/24 any
Deny 192.168.4.0/24 any
Deny 192.168.1.0/24 192.168.4.0/24
Deny any any
Which of the following restrictions is the MOST likely cause?
They have no problem accessing those applications at the beginning of the month.
Network information:
DMZ network-192.168.5.0/24
VPN network-192.168.1.0/24
Datacenter-192.168.2.0/24
User network-192.168.3.0/24
HR network-192.168.4.0/24
Warehouse network-192.168.6.0/24
Finance network 192.168.7.0/24
Traffic shaper configuration:
VLAN Bandwidth limit (Mbps)
VPN 50
User 175
HR 220
Finance 230
Warehouse 75
Guest 50
External firewall allows all networks to access the Internet.
Internal Firewall Rules:
ActionSourceDestination
Permit 192.168.1.0/24 192.168.2.0/24
Permit 192.168.1.0/24 192.168.3.0/24
Permit 192.168.1.0/24 192.168.5.0/24
Permit 192.168.2.0/24 192.168.1.0/24
Permit 192.168.3.0/24 192.168.1.0/24
Permit 192.168.5.0/24 192.168.1.0/24
Permit 192.168.4.0/24 192.168.7.0/24
Permit 192.168.7.0/24 192.168.4.0/24
Permit 192.168.7.0/24 any
Deny 192.168.4.0/24 any
Deny 192.168.1.0/24 192.168.4.0/24
Deny any any
Which of the following restrictions is the MOST likely cause?
Question 449
A pentester must attempt to crack passwords on a windows domain that enforces strong complex passwords.
Which of the following would crack the MOST passwords in the shortest time period?
Which of the following would crack the MOST passwords in the shortest time period?
Question 450
An organization is deploying IoT locks, sensors, and cameras, which operate over 802.11, to replace legacy building access control systems. These devices are capable of triggering physical access changes, including locking and unlocking doors and gates. Unfortunately, the devices have known vulnerabilities for which the vendor has yet to provide firmware updates.
Which of the following would BEST mitigate this risk?
Which of the following would BEST mitigate this risk?

