Question 441
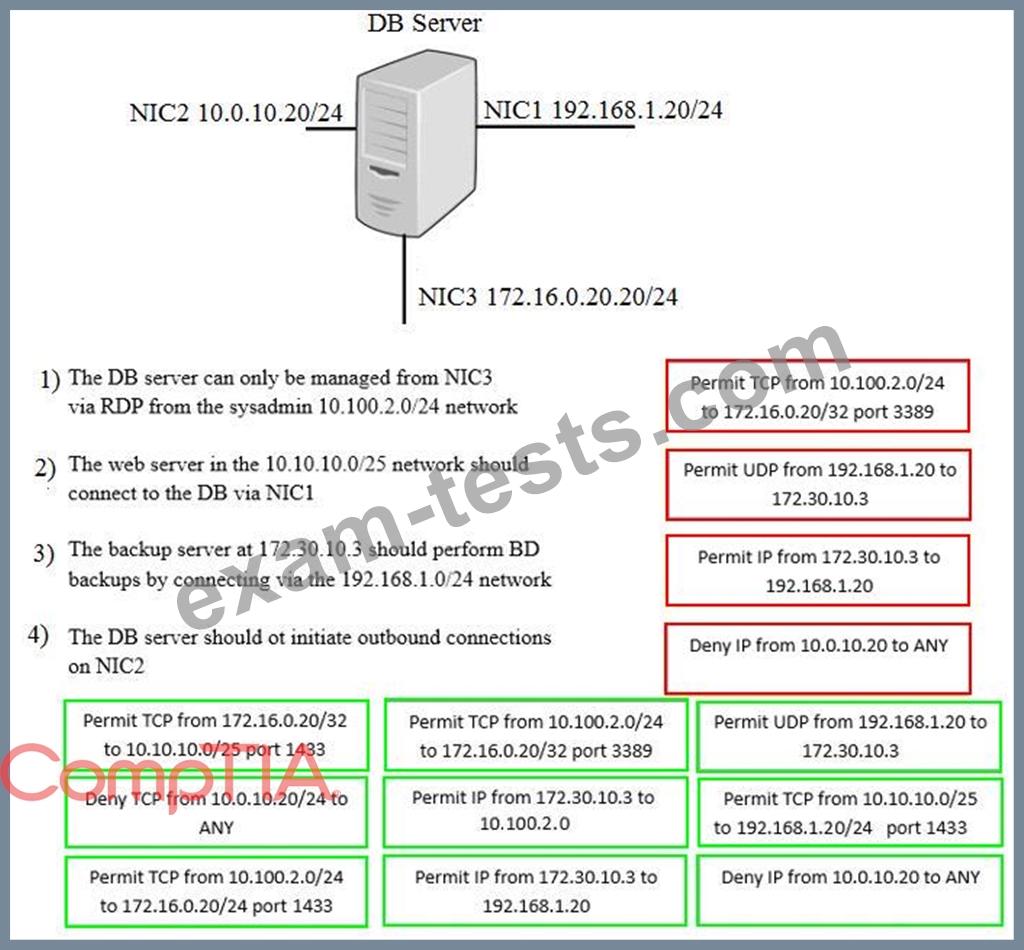
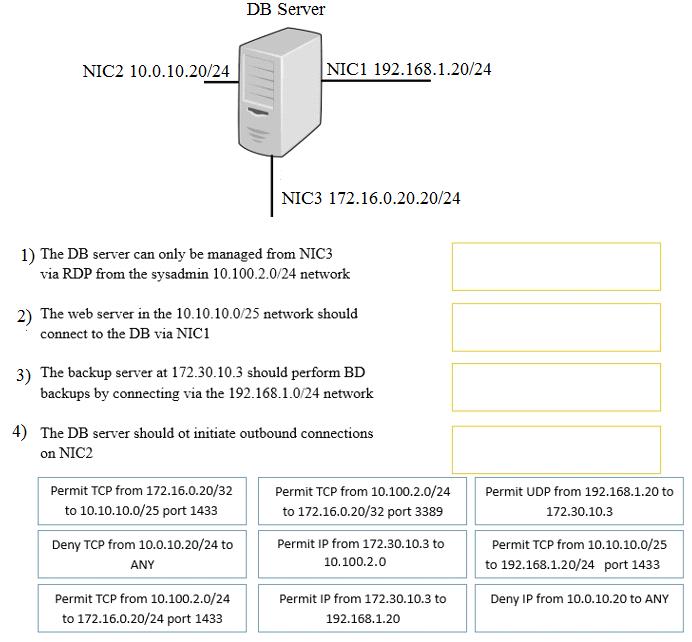
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Question 442
A security analyst is responsible for the completion of a vulnerability assessment at a regional healthcare facility The analyst reviews the following Nmap output:
nmap -v -p scription=SMB-check-value ---scription-ags=unsafe =1 192.168.1.0/24 Which of the following is MOST likely what the security analyst is reviewing?
nmap -v -p scription=SMB-check-value ---scription-ags=unsafe =1 192.168.1.0/24 Which of the following is MOST likely what the security analyst is reviewing?
Question 443
An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security anal... reviewing vulnerability scan result from a recent web server scan.
Portions of the scan results are shown below:
Finding# 5144322
First time detected 10 nov 2015 09:00 GMT_0600
Last time detected 10 nov 2015 09:00 GMT_0600
CVSS base: 5
Access path: http://myorg.com/mailinglist.htm
Request: GET http://mailinglist.aspx?content=volunteer
Response: C:\Docments\MarySmith\malinglist.pdf
Which of the following lines indicates information disclosure about the host that needs to be remediated?
Portions of the scan results are shown below:
Finding# 5144322
First time detected 10 nov 2015 09:00 GMT_0600
Last time detected 10 nov 2015 09:00 GMT_0600
CVSS base: 5
Access path: http://myorg.com/mailinglist.htm
Request: GET http://mailinglist.aspx?content=volunteer
Response: C:\Docments\MarySmith\malinglist.pdf
Which of the following lines indicates information disclosure about the host that needs to be remediated?
Question 444
After significant vulnerabilities and misconfigurations were found in numerous production web applications, a security manager identified the need to implement better development controls.
Which of the following controls should be verified? (Choose two.)
Which of the following controls should be verified? (Choose two.)
Question 445
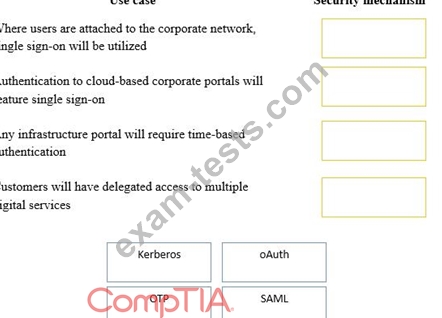
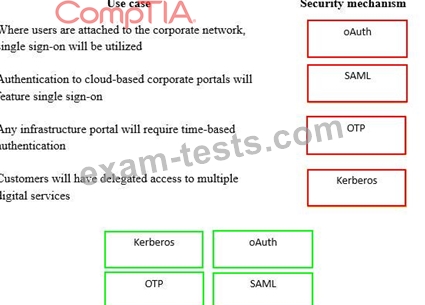
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.