Question 466
A user is suspected of engaging in potentially illegal activities. Law enforcement has requested that the user continue to operate on the network as normal. However, they would like to have a copy of any communications from the user involving certain key terms. Additionally, the law enforcement agency has requested that the user's ongoing communication be retained in the user's account for future investigations.
Which of the following will BEST meet the goals of law enforcement?
Which of the following will BEST meet the goals of law enforcement?
Question 467
A security engineer is analyzing an application during a security assessment to ensure it is configured to protect against common threats. Given the output below:
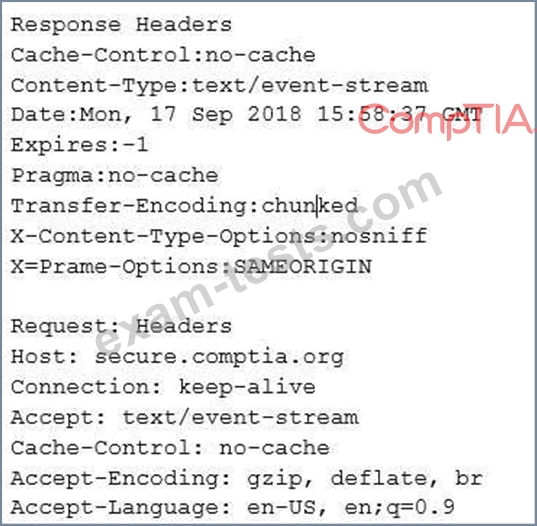
Which of the following tools did the security engineer MOST likely use to generate this output?

Which of the following tools did the security engineer MOST likely use to generate this output?
Question 468
To meet a SLA, which of the following documents should be drafted, defining the company's internal interdependent unit responsibilities and delivery timelines.
Question 469
Given the following information about a company's internal network:
User IP space: 192.168.1.0/24
Server IP space: 192.168.192.0/25
A security engineer has been told that there are rogue websites hosted outside of the proper server space, and those websites need to be identified.
Which of the following should the engineer do?
User IP space: 192.168.1.0/24
Server IP space: 192.168.192.0/25
A security engineer has been told that there are rogue websites hosted outside of the proper server space, and those websites need to be identified.
Which of the following should the engineer do?
Question 470
An architect was recently hired by a power utility to increase the security posture of the company's power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability?
(Choose two.)
(Choose two.)

