Question 201
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the following:
* High-impact controls implemented: 6 out of 10
* Medium-impact controls implemented: 409 out of 472
* Low-impact controls implemented: 97 out of 1000
The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
* Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000
* Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
* High-impact controls implemented: 6 out of 10
* Medium-impact controls implemented: 409 out of 472
* Low-impact controls implemented: 97 out of 1000
The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
* Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000
* Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
Question 202
Given the following:
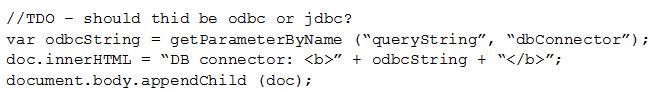
Which of the following vulnerabilities is present in the above code snippet?

Which of the following vulnerabilities is present in the above code snippet?
Question 203
A security administrator wants to allow external organizations to cryptographically validate the company's
domain name in email messages sent by employees. Which of the following should the security
administrator implement?
domain name in email messages sent by employees. Which of the following should the security
administrator implement?
Question 204
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot.
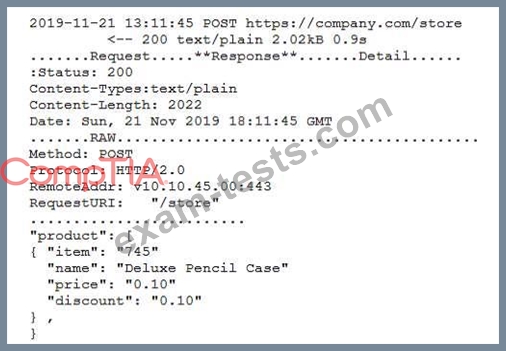
Which of the following tools was MOST likely used to exploit the application?

Which of the following tools was MOST likely used to exploit the application?
Question 205
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices.
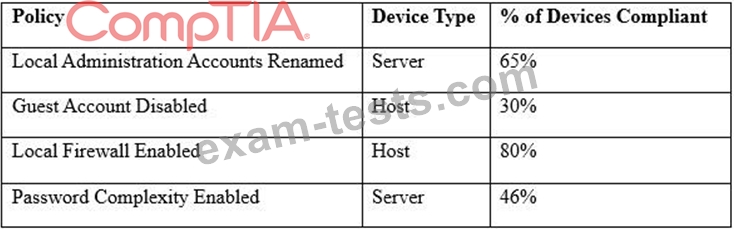
Which of the following tools is the security engineer using to produce the above output?

Which of the following tools is the security engineer using to produce the above output?

