Question 181
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the following:
High-impact controls implemented: 6 out of 10

Medium-impact controls implemented: 409 out of 472

Low-impact controls implemented: 97 out of 1000

The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control

gap: $95,000
Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact

control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
High-impact controls implemented: 6 out of 10

Medium-impact controls implemented: 409 out of 472

Low-impact controls implemented: 97 out of 1000

The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control

gap: $95,000
Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact

control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
Question 182
A security analyst is reviewing the following pseudo-output snippet after running the command less /tmp/ file.tmp.

The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?

The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
Question 183
Engineers at a company believe a certain type of data should be protected from competitors, but the data owner insists the information is not sensitive. An information security engineer is implementing controls to secure the corporate SAN. The controls require dividing data into four groups: non-sensitive, sensitive but accessible, sensitive but export-controlled, and extremely sensitive.
Which of the following actions should the engineer take regarding the data?
Which of the following actions should the engineer take regarding the data?
Question 184
A security engineer is employed by a hospital that was recently purchased by a corporation. Throughout the acquisition process, all data on the virtualized file servers must be shared by departments within both organizations. The security engineer considers data ownership to determine:
Question 185
Ann, a security administrator, is conducting an assessment on a new firewall, which was placed at the perimeter of a network containing PII. Ann runs the following commands on a server (10.0.1.19) behind the firewall:
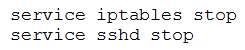
From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:
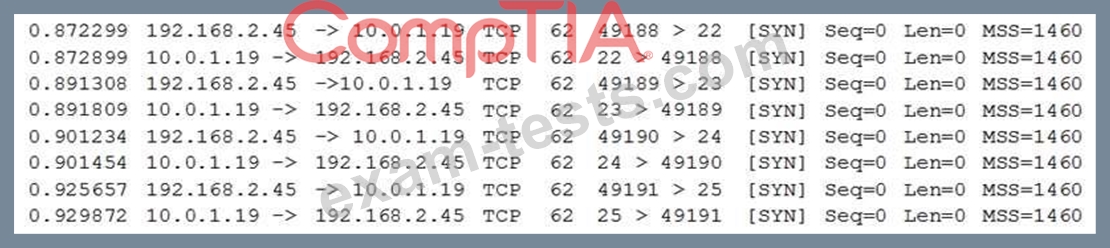
Connectivity to the server from outside the firewall worked as expected prior to executing these commands.
Which of the following can be said about the new firewall?
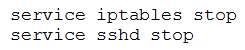
From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:

Connectivity to the server from outside the firewall worked as expected prior to executing these commands.
Which of the following can be said about the new firewall?

