Question 176
A technician is configuring security options on the mobile device manager for users who often utilize public Internet connections while travelling. After ensuring that full disk encryption is enabled, which of the following security measures should the technician take? (Choose two.)
Question 177
A web developer has implemented HTML5 optimizations into a legacy web application. One of the modifications the web developer made was the following client side optimization:
localStorage.setItem("session-cookie", document.cookie);
Which of the following should the security engineer recommend?
localStorage.setItem("session-cookie", document.cookie);
Which of the following should the security engineer recommend?
Question 178
A developer is reviewing the following transaction logs from a web application:
Username: John Doe
Street name: Main St.
Street number: <script>alert(`test')</alert>
Which of the following code snippets should the developer implement given the above transaction logs?
Username: John Doe
Street name: Main St.
Street number: <script>alert(`test')</alert>
Which of the following code snippets should the developer implement given the above transaction logs?
Question 179
Legal authorities notify a company that its network has been compromised for the second time in two years. The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks.
Which of the following would have allowed the security team to use historical information to protect against the second attack?
Which of the following would have allowed the security team to use historical information to protect against the second attack?
Question 180
An organization has established the following controls matrix:
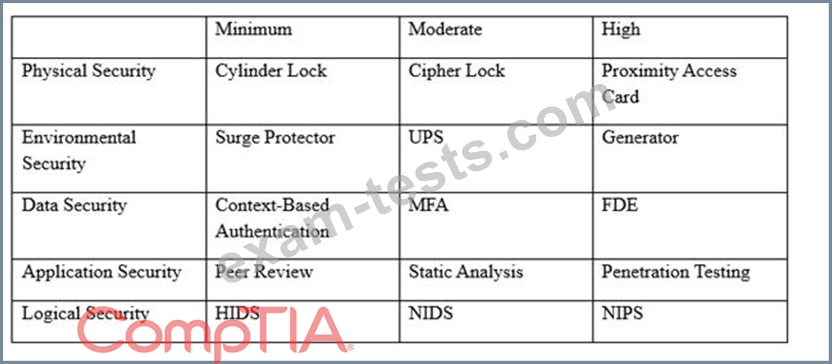
The following control sets have been defined by the organization and are applied in aggregate fashion:
Systems containing PII are protected with the minimum control set.

Systems containing medical data are protected at the moderate level.

Systems containing cardholder data are protected at the high level.

The organization is preparing to deploy a system that protects the confidentially of a database containing
PII and medical data from clients. Based on the controls classification, which of the following controls
would BEST meet these requirements?

The following control sets have been defined by the organization and are applied in aggregate fashion:
Systems containing PII are protected with the minimum control set.

Systems containing medical data are protected at the moderate level.

Systems containing cardholder data are protected at the high level.

The organization is preparing to deploy a system that protects the confidentially of a database containing
PII and medical data from clients. Based on the controls classification, which of the following controls
would BEST meet these requirements?

