Question 316
Given the code snippet below:
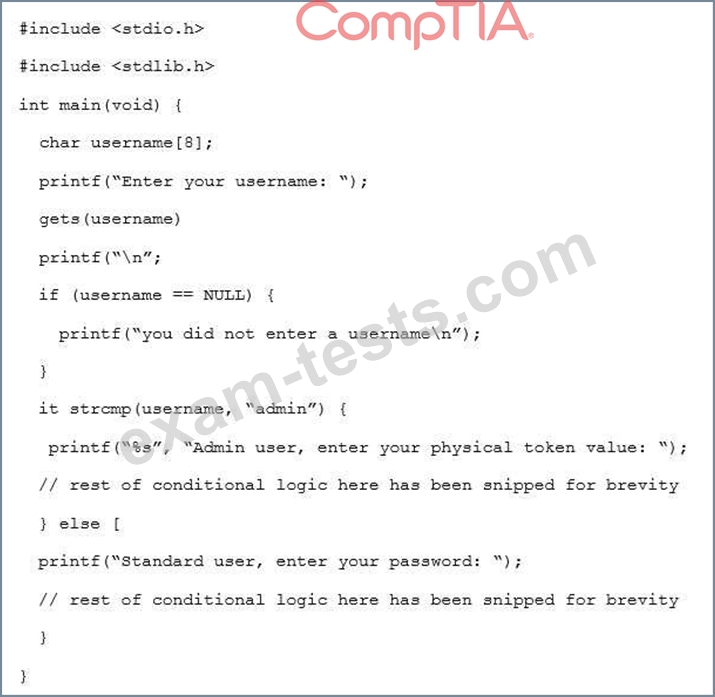
Which of the following vulnerability types in the MOST concerning?

Which of the following vulnerability types in the MOST concerning?
Question 317
The technology steering committee is struggling with increased requirements stemming from an increase in telecommuting. The organization has not addressed telecommuting in the past. The implementation of a new SSL-VPN and a VOIP phone solution enables personnel to work from remote locations with corporate assets. Which of the following steps must the committee take FIRST to outline senior management's directives?
Question 318
A security manager looked at various logs while investigating a recent security breach in the data center from an external source. Each log below was collected from various security devices compiled from a report through the company's security information and event management server.
Logs:
Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:
Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client Log 4:
Encoder oe = new OracleEncoder ();
String query = "Select user_id FROM user_data WHERE user_name = ' "
+ oe.encode ( req.getParameter("userID") ) + " ' and user_password = ' "
+ oe.encode ( req.getParameter("pwd") ) +" ' ";
Vulnerabilities
Buffer overflow
SQL injection
ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select TWO).
Logs:
Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:
Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client Log 4:
Encoder oe = new OracleEncoder ();
String query = "Select user_id FROM user_data WHERE user_name = ' "
+ oe.encode ( req.getParameter("userID") ) + " ' and user_password = ' "
+ oe.encode ( req.getParameter("pwd") ) +" ' ";
Vulnerabilities
Buffer overflow
SQL injection
ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select TWO).
Question 319
A security researches is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds.
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
Question 320
An external red team is brought into an organization to perform a penetration test of a new network-based application. The organization deploying the network application wants the red team to act like remote, external attackers, and instructs the team to use a black-box approach. Which of the following is the BEST methodology for the red team to follow?

