Question 406
Company XYZ has purchased and is now deploying a new HTML5 application. The company wants to hire a penetration tester to evaluate the security of the client and server components of the proprietary web application before launch. Which of the following is the penetration tester MOST likely to use while performing black box testing of the security of the company's purchased application? (Select TWO).
Question 407
An organization has established the following controls matrix:
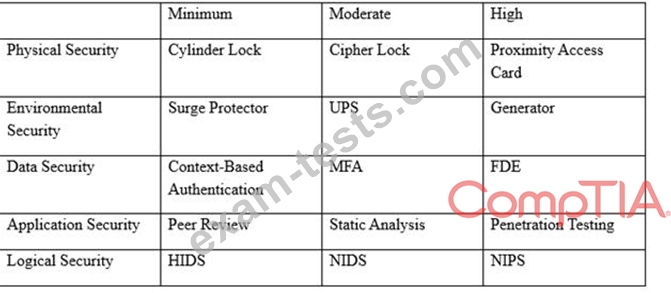
The following control sets have been defined by the organization and are applied in aggregate fashion:
* Systems containing PII are protected with the minimum control set.
* Systems containing medical data are protected at the moderate level.
* Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients.
Based on the controls classification, which of the following controls would BEST meet these requirements?

The following control sets have been defined by the organization and are applied in aggregate fashion:
* Systems containing PII are protected with the minimum control set.
* Systems containing medical data are protected at the moderate level.
* Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients.
Based on the controls classification, which of the following controls would BEST meet these requirements?
Question 408
An assessor identifies automated methods for identifying security control compliance through validating sensors at the endpoint and at Tier 2. Which of the following practices satisfy continuous monitoring of authorized information systems?
Question 409
A security auditor needs to review the manner in which an entertainment device operates. The auditor is analyzing the output of a port scanning tool to determine the next steps in the security review. Given the following log output.
The best option for the auditor to use NEXT is:

The best option for the auditor to use NEXT is:

Question 410
An extensive third-party audit reveals a number of weaknesses m a company's endpoint security posture. The most significant issues are as follows:
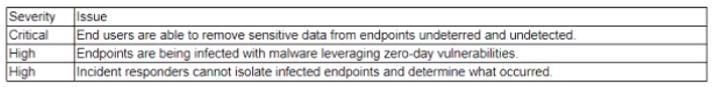
Which of the following endpoint security solutions mitigate the GREATEST amount of risk?

Which of the following endpoint security solutions mitigate the GREATEST amount of risk?

