Question 426
The Information Security Officer (ISO) is reviewing a summary of the findings from the last COOP tabletop exercise. The Chief Information Officer (CIO) wants to determine which additional controls must be implemented to reduce the risk of an extended customer service outage due to the VoIP system being unavailable. Which of the following BEST describes the scenario presented and the document the ISO is reviewing?
Question 427
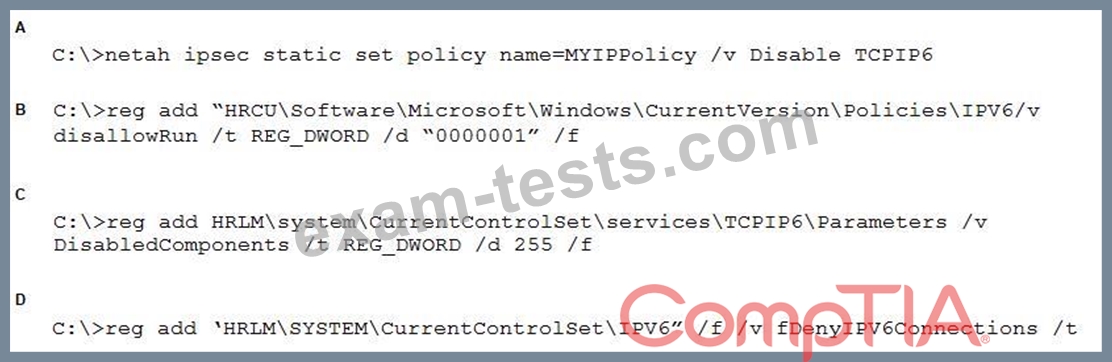
A security analyst, who is working in a Windows environment, has noticed a significant amount of IPv6 traffic originating from a client, even though IPv6 is not currently in use. The client is a stand-alone device, not connected to the AD that manages a series of SCADA devices used for manufacturing. Which of the following is the appropriate command to disable the client's IPv6 stack?

Question 428
The SOC has noticed an unusual volume of traffic coming from an open WiFi guest network that appears correlated with a broader network slowdown The network team is unavailable to capture traffic but logs from network services are available
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
Question 429
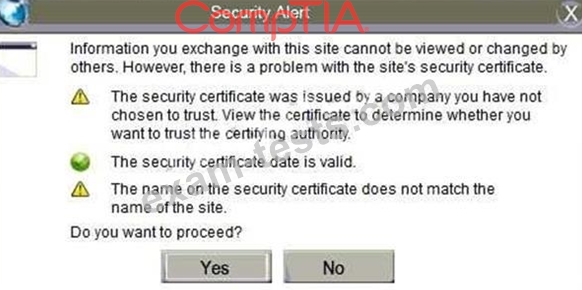
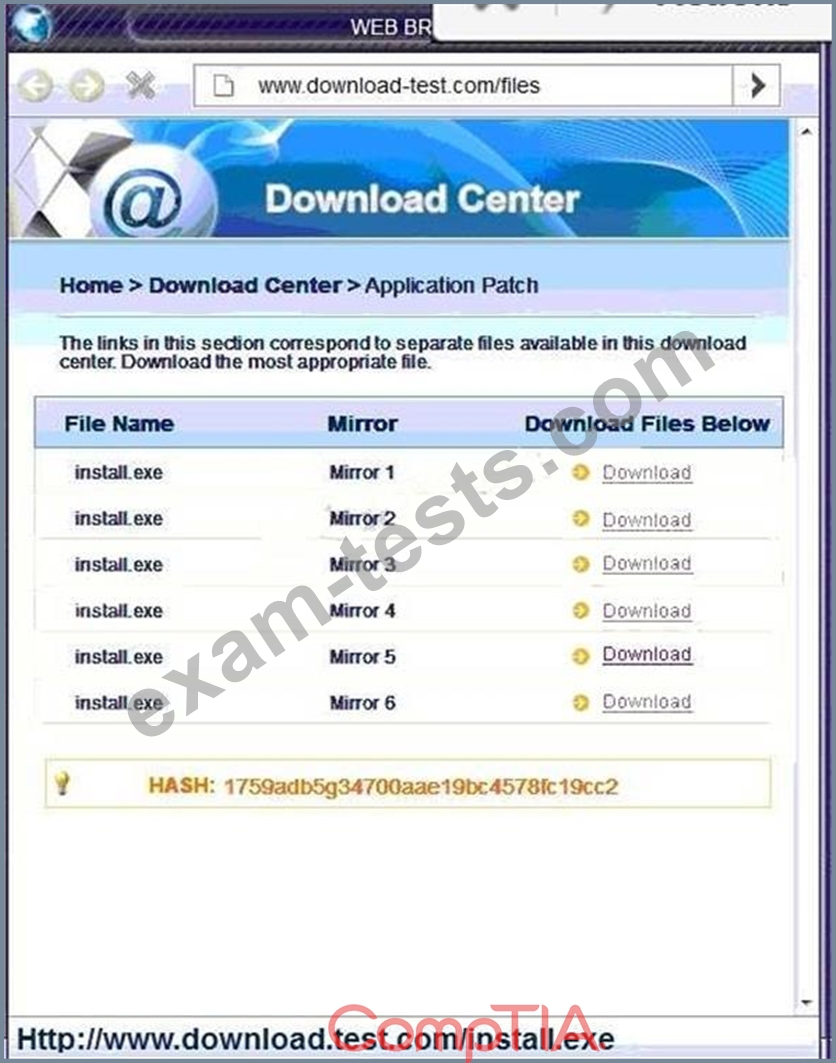
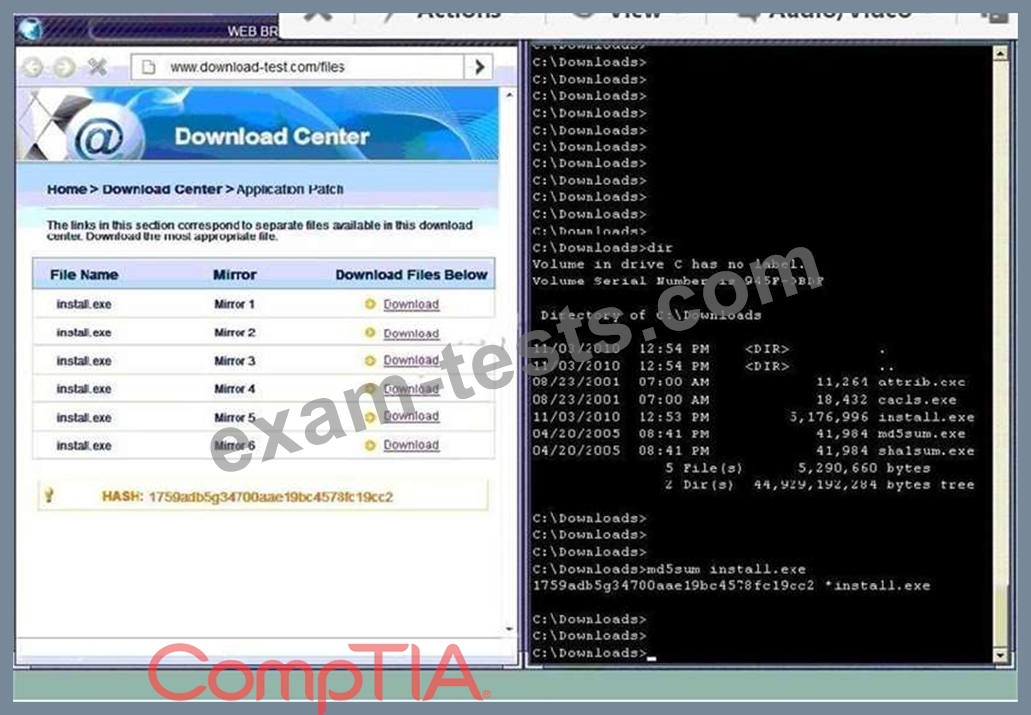
SIMULATION
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
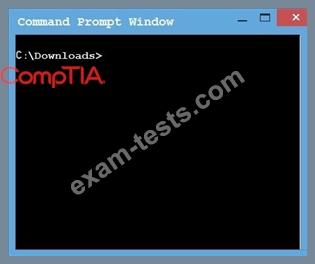
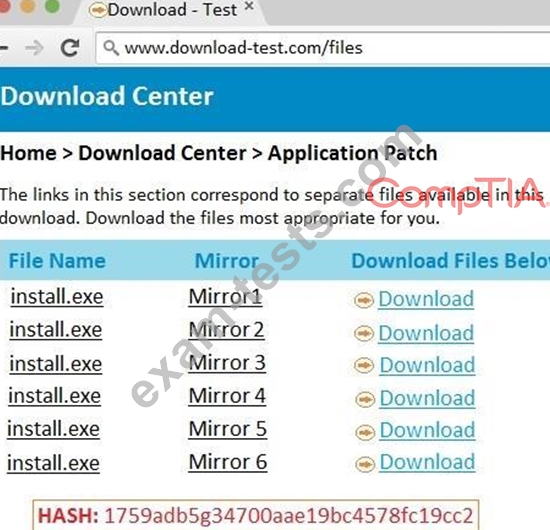
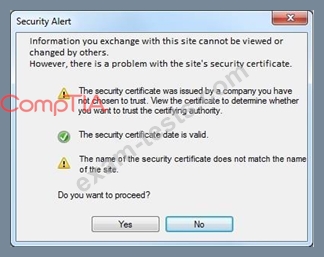
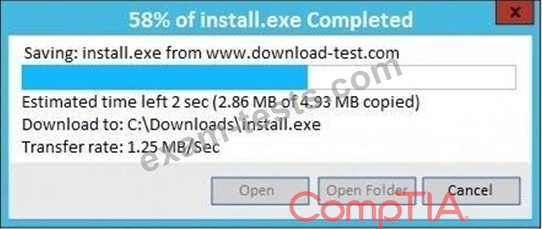
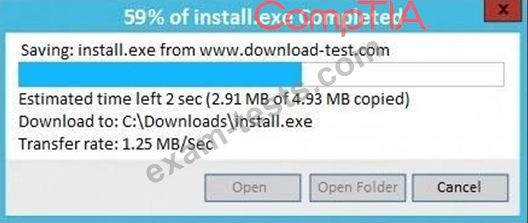
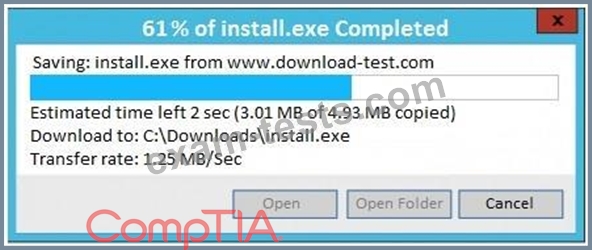
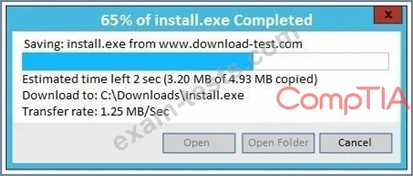
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.







Question 430
An organization is considering the use of a thin clientarchitecture as it moves to a cloud-hosted environment.
A security analyst is asked to provide thoughts on the security advantages of using thin clients and virtual workstations. Which of the following are security advantages of the use of this combinationof thin clients and virtual workstations?
A security analyst is asked to provide thoughts on the security advantages of using thin clients and virtual workstations. Which of the following are security advantages of the use of this combinationof thin clients and virtual workstations?