Question 441
Which of the following types of attacks is the user attempting?
select id, firstname, lastname from authors
User input= firstname= Hack;man
lastname=Johnson
select id, firstname, lastname from authors
User input= firstname= Hack;man
lastname=Johnson
Question 442
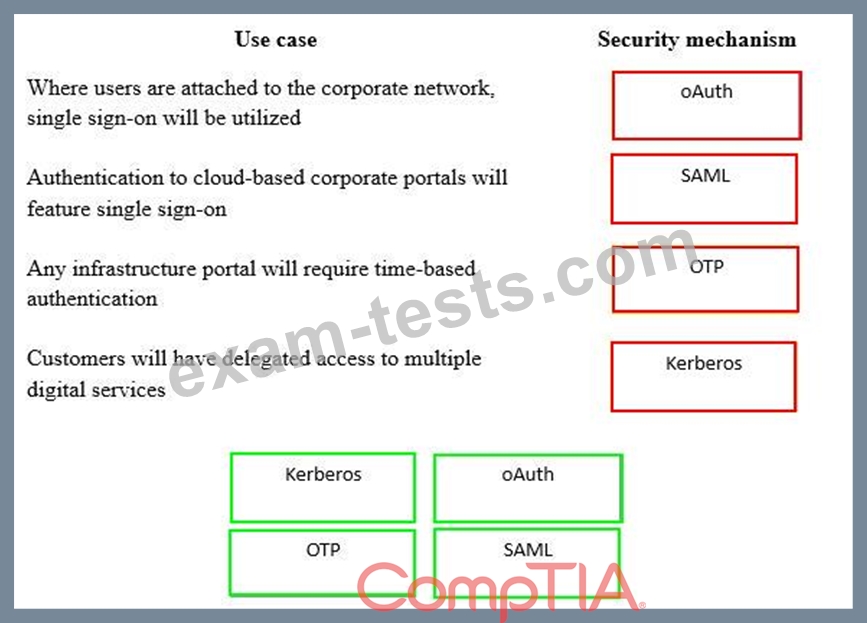
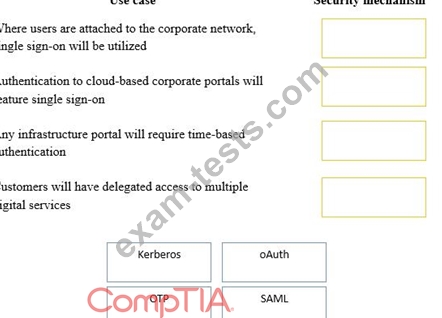
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.

Question 443
After an employee was terminated, the company discovered the employee still had access to emails and attached content that should have been destroyed during the off-boarding. The employee's laptop and cell phone were confiscated and accounts were disabled promptly.
Forensic investigation suggests the company's DLP was effective, and the content in QUESTION
5was not sent outside of work or transferred to removable media. Personality owned devices are not permitted to access company systems or information.
Which of the following would be the MOST efficient control to prevent this from occurring in the future?
Forensic investigation suggests the company's DLP was effective, and the content in QUESTION
5was not sent outside of work or transferred to removable media. Personality owned devices are not permitted to access company systems or information.
Which of the following would be the MOST efficient control to prevent this from occurring in the future?
Question 444
Joe is a security architect who is tasked with choosing a new NIPS platform that has the ability to perform SSL inspection, analyze up to 10Gbps of traffic, can be centrally managed and only reveals inspected application payload data to specified internal security employees. Which of the following steps should Joe take to reach the desired outcome?
Question 445
A company's user community is being adversely affected by various types of emails whose authenticity cannot be trusted. The Chief Information Security Officer (CISO) must address the problem.
Which of the following solutions would BEST support trustworthy communication solutions?
Which of the following solutions would BEST support trustworthy communication solutions?