Question 461
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet:
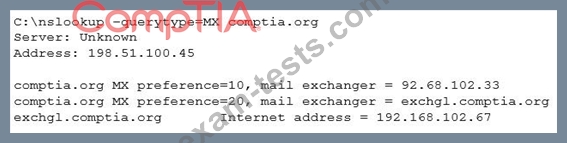
Which of the following should the penetration tester conclude about the command output?

Which of the following should the penetration tester conclude about the command output?
Question 462
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
Question 463
A security administrator wants to implement controls to harden company-owned mobile devices. Company policy specifies the following requirements:
* Mandatory access control must be enforced by the OS.
* Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Select three).
* Mandatory access control must be enforced by the OS.
* Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Select three).
Question 464
An application has been through a peer review and regression testing and is prepared for release. A security engineer is asked to analyze an application binary to look for potential vulnerabilities prior to wide release. After thoroughly analyzing the application, the engineer informs the developer it should include additional input sanitation in the application to prevent overflows. Which of the following tools did the security engineer MOST likely use to determine this recommendation?
Question 465
During the decommissioning phase of a hardware project, a security administrator is tasked with ensuring no sensitive data is released inadvertently. All paper records are scheduled to be shredded in a crosscut shredded, and the waste will be burned. The system drives and removable media have been removed prior to e-cycling the hardware.
Which of the following would ensure no data is recovered from the system droves once they are disposed of?
Which of the following would ensure no data is recovered from the system droves once they are disposed of?

