Question 181
A cybersecurity analyst has several log files to review. Instead of using grep and cat commands, the
analyst decides to find a better approach to analyze the logs. Given a list of tools, which of the following
would provide a more efficient way for the analyst to conduct a timeline analysis, do keyword searches,
and output a report?
analyst decides to find a better approach to analyze the logs. Given a list of tools, which of the following
would provide a more efficient way for the analyst to conduct a timeline analysis, do keyword searches,
and output a report?
Question 182
A project lead is reviewing the statement of work for an upcoming project that is focused on identifying potential weaknesses in the organization's internal and external network infrastructure. As part of the project, a team of external contractors will attempt to employ various attacks against the organization.
The statement of work specifically addresses the utilization of an automated tool to probe network resources in an attempt to develop logical diagrams indication weaknesses in the infrastructure.
The scope of activity as described in the statement of work is an example of:
The statement of work specifically addresses the utilization of an automated tool to probe network resources in an attempt to develop logical diagrams indication weaknesses in the infrastructure.
The scope of activity as described in the statement of work is an example of:
Question 183
A security analyst has been asked to scan a subnet. During the scan, the following output was generated:
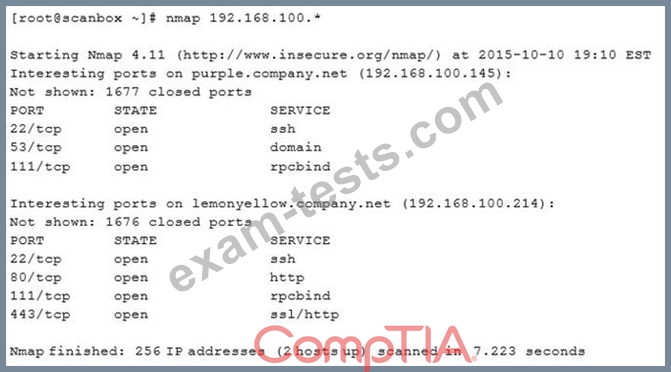
Based on the output above, which of the following is MOST likely?

Based on the output above, which of the following is MOST likely?
Question 184
An analyst has received unusual alerts on the SIEM dashboard. The analyst wants to get payloads that the hackers are sending toward the target systems without impacting the business operation. Which of the following should the analyst implement?
Question 185
A technician recently fixed a computer with several viruses and spyware programs on it and notices the Internet settings were set to redirect all traffic through an unknown proxy. This type of attack is known as which of the following?

