Question 46
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:
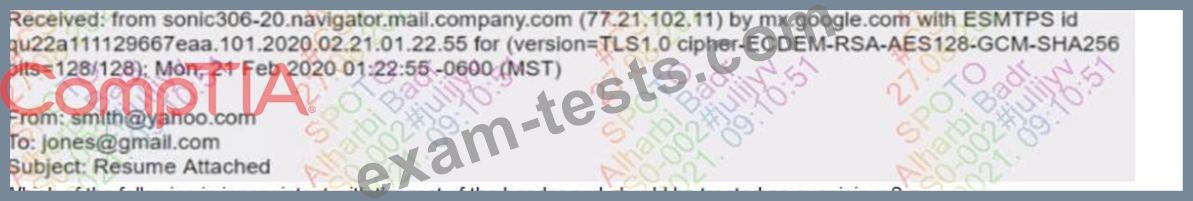
Which of the following is inconsistent with the rest of the header and should be treated as suspicious?

Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
Question 47
A forensics investigator is analyzing a compromised workstation. The investigator has cloned the hard drive and needs to verify that a bit-level image copy of a hard drive is an exact clone of the original hard drive that was collected as evidence. Which of the following should the investigator do?
Question 48
A social media company is planning an acquisition. Prior to the purchase, the Chief Security Officer (CSO) would like a full report to gain a better understanding of the prospective company's cybersecurity posture and to identify risks in the supply chain. Which of the following will best support the CSO's objective?
Question 49
A security analyst is reviewing the network security monitoring logs listed below:
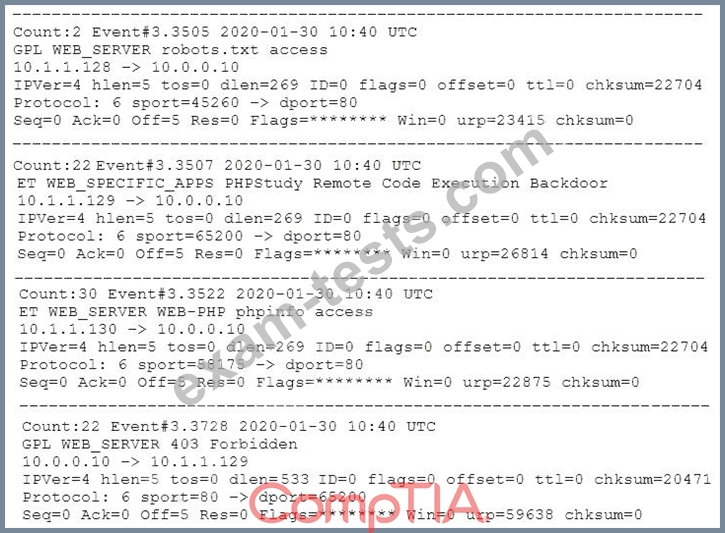
Which of the following is the analyst MOST likely observing? (Select TWO).

Which of the following is the analyst MOST likely observing? (Select TWO).
Question 50
A SIEM analyst noticed a spike in activities from the guest wireless network to several electronic health record (EHR) systems. After further analysis, the analyst discovered that a large volume of data has been uploaded to a cloud provider in the last six months. Which of the following actions should the analyst do FIRST?

