Question 56
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
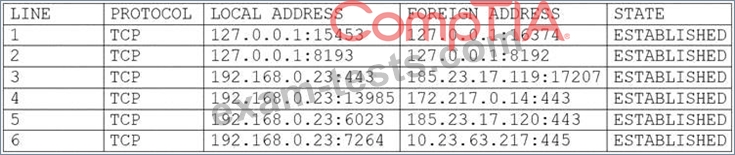
Which of the following lines indicates the computer may be compromised?

Which of the following lines indicates the computer may be compromised?
Question 57
A security analyst is attempting to utilize the blowing threat intelligence for developing detection capabilities:

In which of the following phases is this APT MOST likely to leave discoverable artifacts?

In which of the following phases is this APT MOST likely to leave discoverable artifacts?
Question 58
A financial organization has offices located globally. Per the organization's policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's dat
a. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
a. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
Question 59
A security analyst is reviewing the following DNS logs as part of security-monitoring activities:
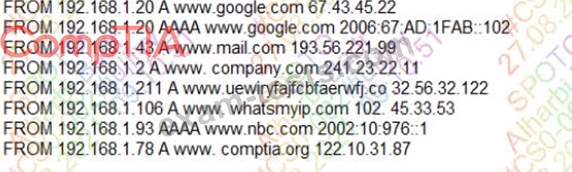
Which of the following MOST likely occurred?

Which of the following MOST likely occurred?
Question 60
An organization has the following risk mitigation policy:
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
All other prioritization will be based on risk value.
The organization has identified the following risks:
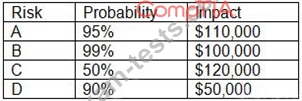
Which of the following is the order of priority for risk mitigation from highest to lowest?
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
All other prioritization will be based on risk value.
The organization has identified the following risks:

Which of the following is the order of priority for risk mitigation from highest to lowest?

