Question 51
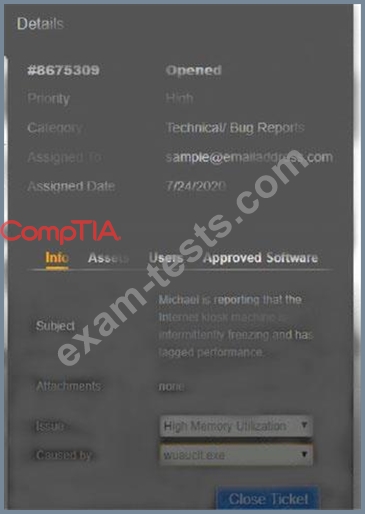
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
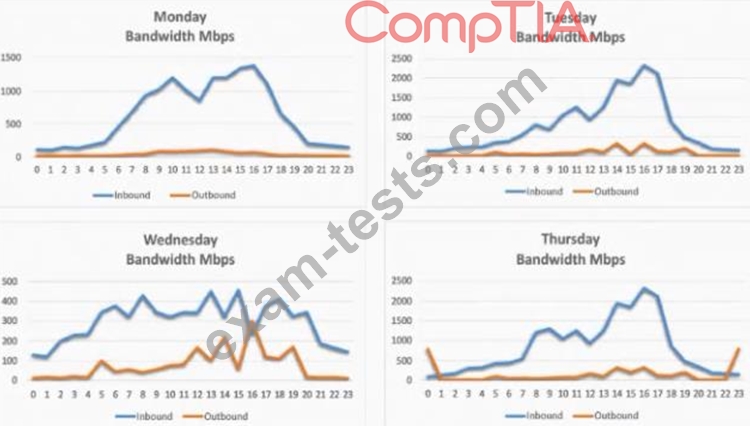
Which of the following should the analyst review to find out how the data was exfilltrated?

Which of the following should the analyst review to find out how the data was exfilltrated?
Question 52
A company has a cluster of web servers that is critical to the business. A systems administrator installed a utility to troubleshoot an issue, and the utility caused the entire cluster to 90 offline. Which of the following solutions would work BEST prevent to this from happening again?
Question 53
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue.
INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu If at any time you would like to bring back the initial state of the simulation, please click the Reset All button
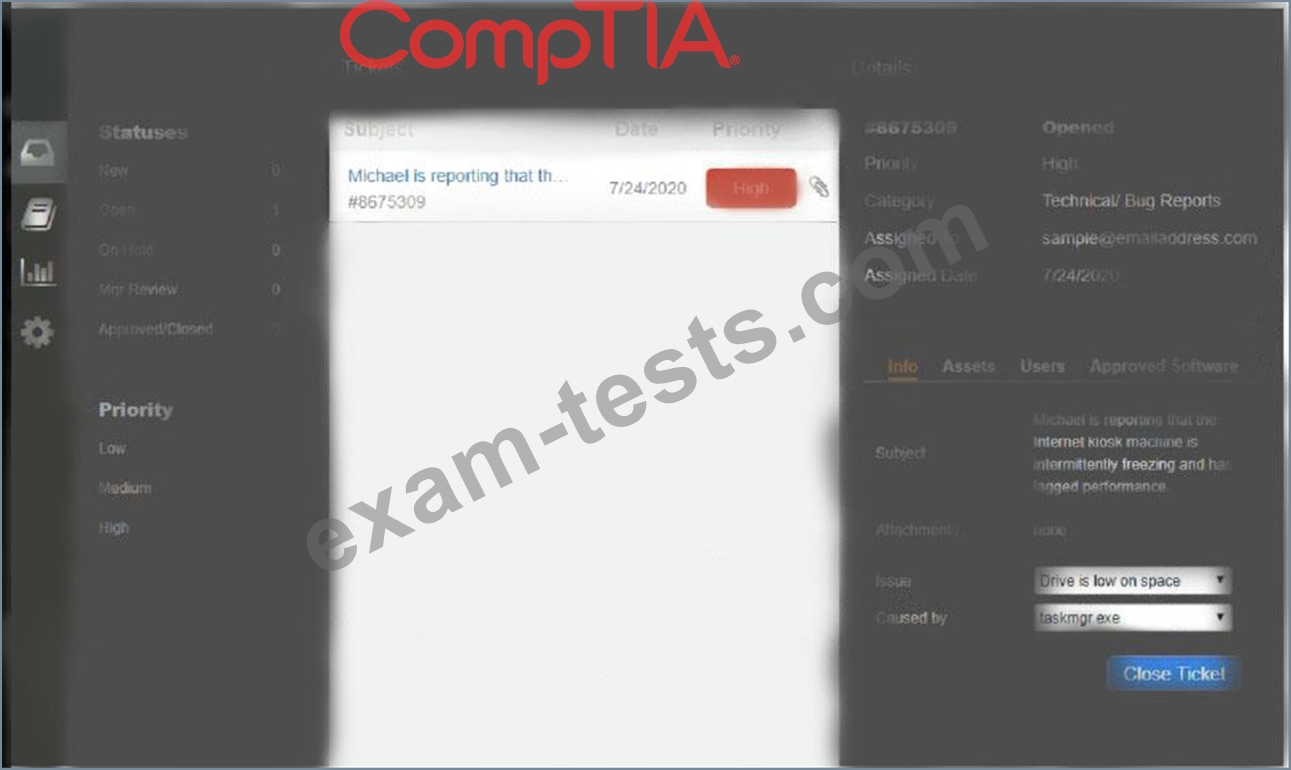
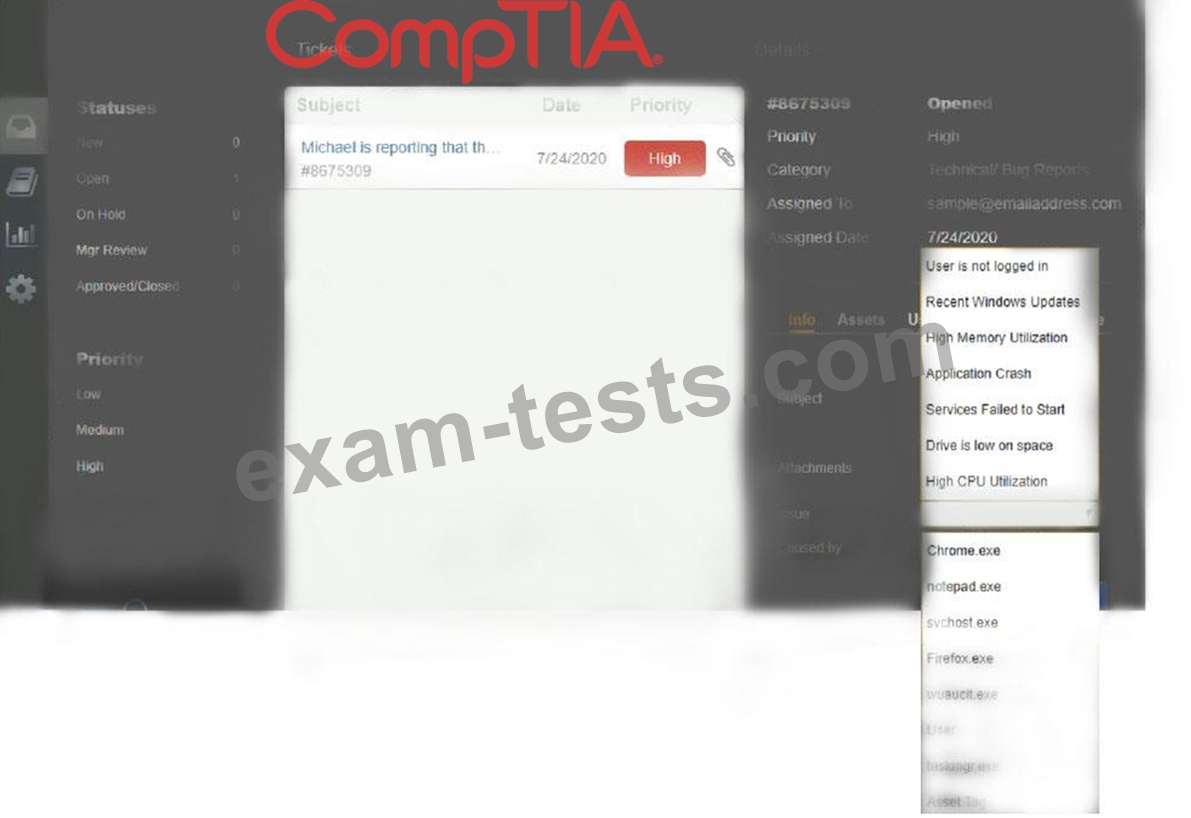
INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu If at any time you would like to bring back the initial state of the simulation, please click the Reset All button


Question 54
A company's change management team has asked a security analyst to review a potential change to the email server before it is released into production. The analyst reviews the following change request:
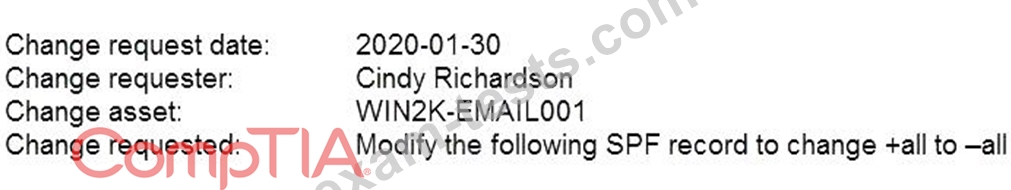
Which of the following is the MOST likely reason for the change?

Which of the following is the MOST likely reason for the change?
Question 55
An organization developed a comprehensive modern response policy Executive management approved the policy and its associated procedures. Which of the following activities would be MOST beneficial to evaluate personnel's familiarity with incident response procedures?