Question 71
In SIEM software, a security analysis selected some changes to hash signatures from monitored files during the night followed by SMB brute-force attacks against the file servers Based on this behavior, which of the following actions should be taken FIRST to prevent a more serious compromise?
Question 72
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to devices within the ICS environment without compromising security.
To provide the MOST secure access model in this scenario, the jumpbox should be.
To provide the MOST secure access model in this scenario, the jumpbox should be.
Question 73
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company The text of one of the emails is shown below:
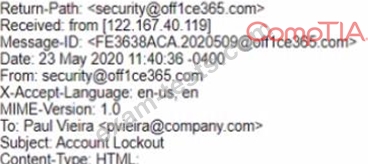
Office 365 User.
It looks like you account has been locked out Please click this <a href=Tittp7/accountfix-office356 com/login php">link</a> and follow the pfompts to restore access Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?

Office 365 User.
It looks like you account has been locked out Please click this <a href=Tittp7/accountfix-office356 com/login php">link</a> and follow the pfompts to restore access Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?
Question 74
A security analyst who works in the SOC receives a new requirement to monitor for indicators of compromise. Which of the following is the first action the analyst should take in this situation?
Question 75
A security analyst is adding input to the incident response communication plan.
A company officer has suggested that if a data breach occurs, only affected parties should be notified to keep an incident from becoming a media headline.
Which of the following should the analyst recommend to the company officer?
A company officer has suggested that if a data breach occurs, only affected parties should be notified to keep an incident from becoming a media headline.
Which of the following should the analyst recommend to the company officer?

