Question 81
Which of the following would MOST likely be included in the incident response procedure after a security breach of customer PII?
Question 82
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host. The analyst queries for IP 192.168.50.2 for a 24-hour period:
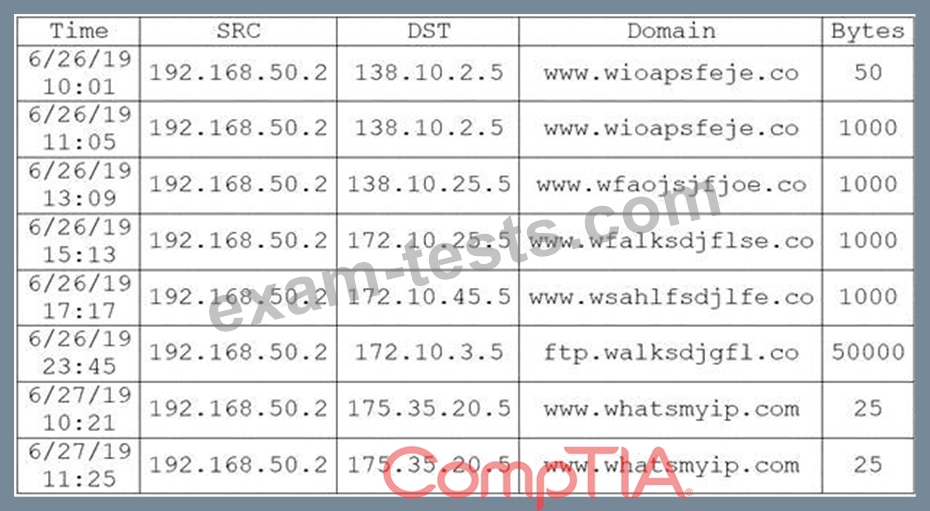
To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and.

To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and.
Question 83
A security analyst needs to determine the best method for securing access to a top-secret datacenter Along with an access card and PIN code, which of the following additional authentication methods would be BEST to enhance the datacenter's security?
Question 84
A vulnerability scan came back with critical findings for a Microsoft SharePoint server:
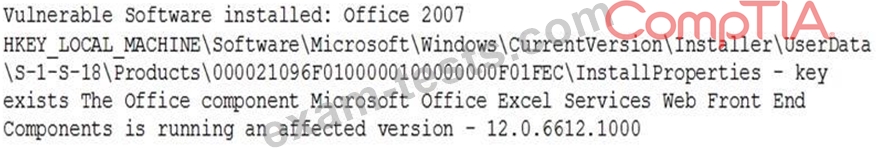
Which of the following actions should be taken?

Which of the following actions should be taken?
Question 85
A security analyst needs to provide the development learn with secure connectivity from the corporate network to a three-tier cloud environment. The developers require access to servers in all three tiers in order to perform various configuration tasks. Which of the following technologies should the analyst implement to provide secure transport?

