Question 96
During a review of SIEM alerts, a securrty analyst discovers the SIEM is receiving many alerts per day from the file-integrity monitoring toot about files from a newly deployed application that should not change. Which of the following steps should the analyst complete FIRST to respond to the issue7
Question 97
Which of the following is a vulnerability that is specific to hypervisors?
Question 98
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results:
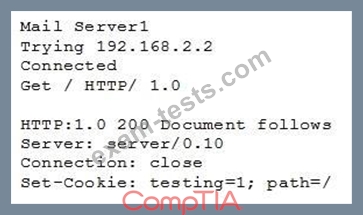
Which of the following describes the output of this scan?

Which of the following describes the output of this scan?
Question 99
When reviewing a compromised authentication server, a security analyst discovers the following hidden file:
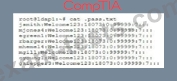
Further analysis shows these users never logged in to the server. Which of the following types of attacks was used to obtain the file and what should the analyst recommend to prevent this type of attack from reoccurring?

Further analysis shows these users never logged in to the server. Which of the following types of attacks was used to obtain the file and what should the analyst recommend to prevent this type of attack from reoccurring?
Question 100
A security analyst is investigate an no client related to an alert from the threat detection platform on a host (10.0 1.25) in a staging environment that could be running a cryptomining tool because it in sending traffic to an IP address that are related to Bitcoin.
The network rules for the instance are the following:
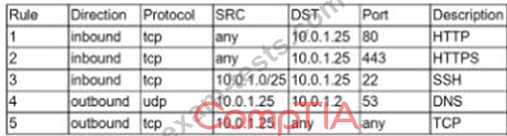
Which of the following is the BEST way to isolate and triage the host?
The network rules for the instance are the following:

Which of the following is the BEST way to isolate and triage the host?

