Question 106
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
Which of the following actions should the technician take to accomplish this task?
Question 107
A security analyst is reviewing the following Internet usage trend report:
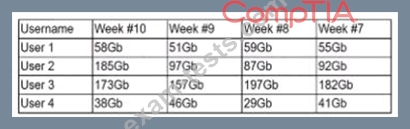
Which of the following usernames should the security analyst investigate further?

Which of the following usernames should the security analyst investigate further?
Question 108
During a routine review of service restarts a security analyst observes the following in a server log:
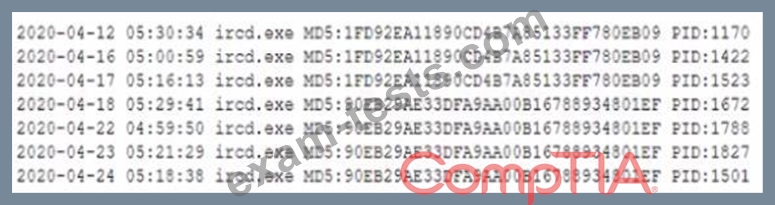
Which of the following is the GREATEST security concern?

Which of the following is the GREATEST security concern?
Question 109
Forming a hypothesis, looking for indicators of compromise, and using the findings to proactively improve detection capabilities are examples of the value of:
Question 110
Given the following access log:
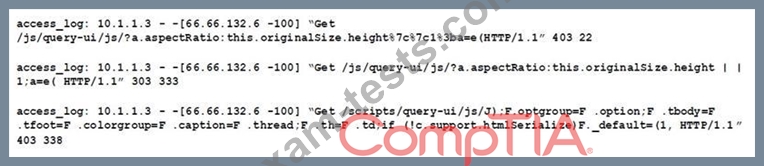
Which of the following accurately describes what this log displays?

Which of the following accurately describes what this log displays?

