Question 231
A project lead is reviewing the statement of work for an upcoming project that is focused on identifying potential weaknesses in the organization's internal and external network infrastructure.
As part of the project, a team of external contractors will attempt to employ various attacks against the organization. The statement of work specifically addresses the utilization of an automated tool to probe network resources in an attempt to develop logical diagrams indication weaknesses in the infrastructure.
The scope of activity as described in the statement of work is an example of:
As part of the project, a team of external contractors will attempt to employ various attacks against the organization. The statement of work specifically addresses the utilization of an automated tool to probe network resources in an attempt to develop logical diagrams indication weaknesses in the infrastructure.
The scope of activity as described in the statement of work is an example of:
Question 232
The Chief Information Security Officer (CISO) has asked the security analyst to examine abnormally high processor utilization on a key server. The output below is from the company's research and development (R&D) server.
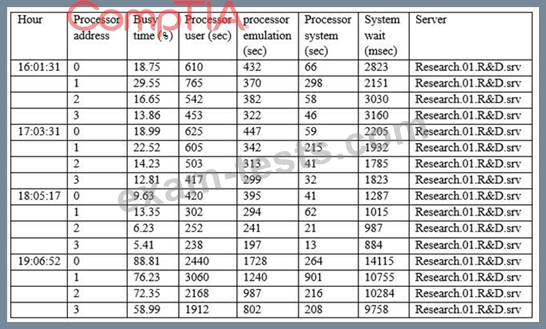
Which of the following actions should the security analyst take FIRST?

Which of the following actions should the security analyst take FIRST?
Question 233
A cybersecurity analyst is currently auditing a new Active Directory server for compliance. The analyst uses Nessus to do the initial scan, and Nessus reports the following:
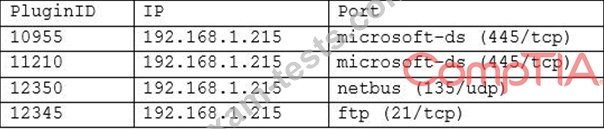
Which of the following critical vulnerabilities has the analyst discovered?

Which of the following critical vulnerabilities has the analyst discovered?
Question 234
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following:

The analyst runs the following command next:
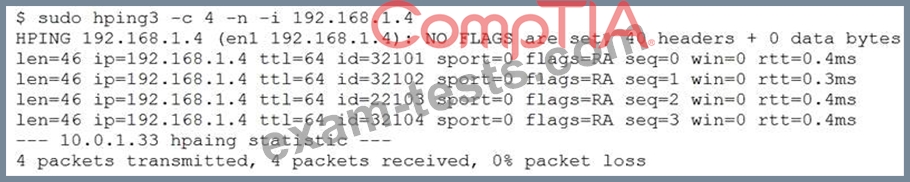
Which of the following would explain the difference in results?

The analyst runs the following command next:

Which of the following would explain the difference in results?
Question 235
Data spillage occurred when an employee accidentally emailed a sensitive file to an external recipient.
Which of the following controls would have MOST likely prevented this incident?
Which of the following controls would have MOST likely prevented this incident?

