Question 221
The Chief Information Officer (CIO) for a large manufacturing organization has noticed a significant number of unknown devices with possible malware infections are on the organization's corporate network.
Which of the following would work BEST to prevent the issue?
Which of the following would work BEST to prevent the issue?
Question 222
A security analyst is investigating a compromised Linux server.
The analyst issues the ps command and receives the following output.
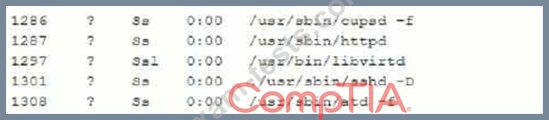
Which of the following commands should the administrator run NEXT to further analyze the compromised system?
The analyst issues the ps command and receives the following output.

Which of the following commands should the administrator run NEXT to further analyze the compromised system?
Question 223
The IT department at a growing law firm wants to begin using a third-party vendor for vulnerability monitoring and mitigation. The executive director of the law firm wishes to outline the assumptions and expectations between the two companies. Which of the following documents might be referenced in the event of a security breach at the law firm?
Question 224
A cybersecurity analyst is reviewing log data and sees the output below:
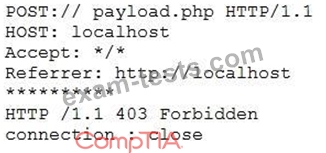
Which of the following technologies MOST likely generated this log?

Which of the following technologies MOST likely generated this log?
Question 225
A system administrator has reviewed the following output:
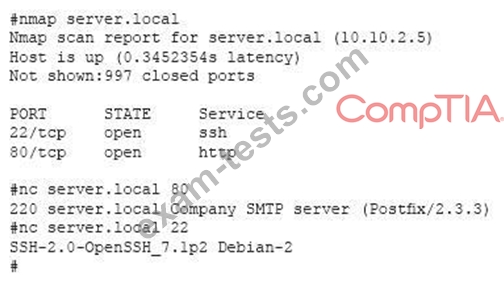
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?

