Question 241
A security analyst is reviewing the following log from an email security service.
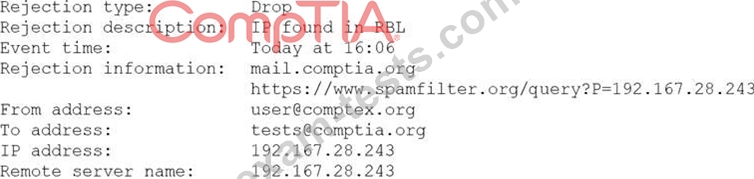
Which of the following BEST describes the reason why the email was blocked?

Which of the following BEST describes the reason why the email was blocked?
Question 242
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following:

The analyst runs the following command next:
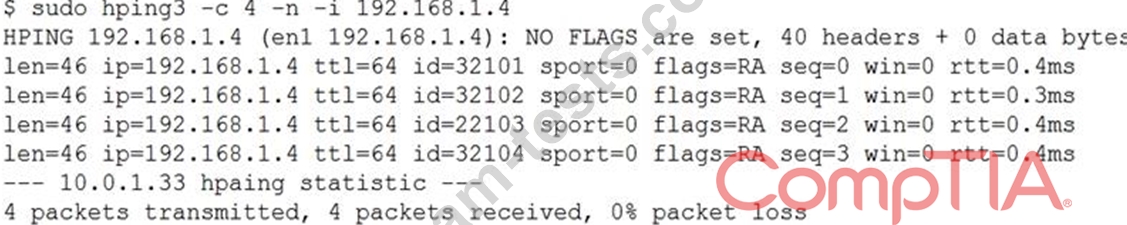
Which of the following would explain the difference in results?

The analyst runs the following command next:

Which of the following would explain the difference in results?
Question 243
Which of the following attacks can be prevented by using output encoding?
Question 244
A security analyst needs to obtain the footprint of the network. The footprint must identify the following information;
* TCP and UDP services running on a targeted system
* Types of operating systems and versions
* Specific applications and versions
Which of the following tools should the analyst use to obtain the data?
* TCP and UDP services running on a targeted system
* Types of operating systems and versions
* Specific applications and versions
Which of the following tools should the analyst use to obtain the data?
Question 245
Which of the following sets of attributes BEST illustrates the characteristics of an insider threat from a security perspective?

