Question 231
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
Question 232
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
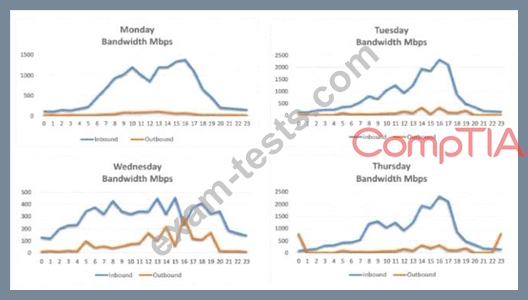
Which of the following should the analyst review to find out how the data was exfilltrated?

Which of the following should the analyst review to find out how the data was exfilltrated?
Question 233
A security analyst receives an alert from the SIEM about a possible attack happening on the network The analyst opens the alert and sees the IP address of the suspected server as 192.168.54.66. which is part of the network 192 168 54 0/24. The analyst then pulls all the command history logs from that server and sees the following
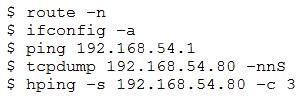
Which of the following activities is MOST likely happening on the server?

Which of the following activities is MOST likely happening on the server?
Question 234
An information security analyst is compiling data from a recent penetration test and reviews the following output:
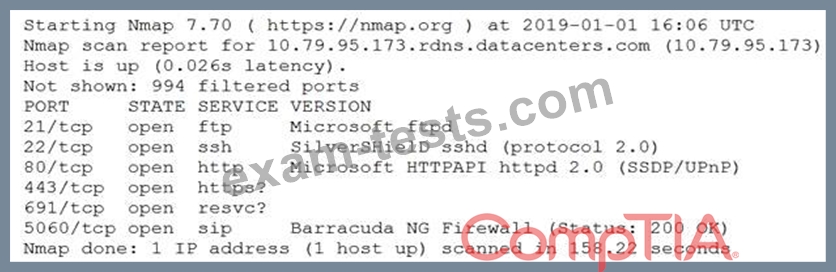
The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?

The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?
Question 235
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
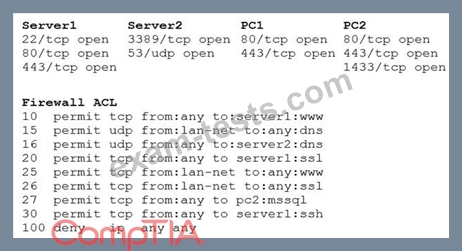
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

