Question 246
A security analyst reviews SIEM logs and detects a well-known malicious executable running in a Windows machine The up-to-date antivirus cannot detect the malicious executable Which of the following is the MOST likely cause of this issue?
Question 247
A development team uses open-source software and follows an Agile methodology with two-week sprints.
Last month, the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
Last month, the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
Question 248
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities. The type of vulnerability that should be disseminated FIRST is one that:
Question 249
After reviewing the following packet, a cybersecurity analyst has discovered an unauthorized service is running on a company's computer.
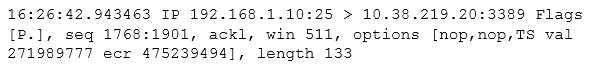
Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?

Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?
Question 250
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
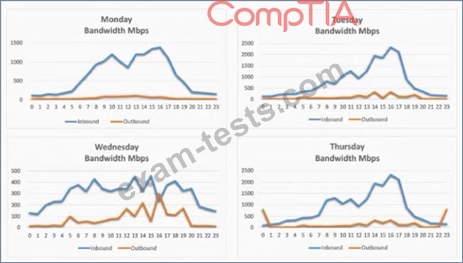
Which of the following should the analyst review to find out how the data was exfilltrated?

Which of the following should the analyst review to find out how the data was exfilltrated?

