Question 251
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
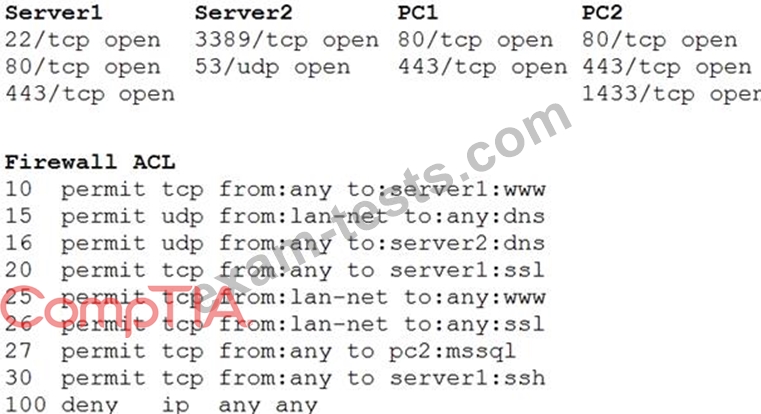
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?

Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
Question 252
An analyst is examining a system that is suspected of being involved in an intrusion.
The analyst uses the command `cat/etc/passwd' and receives the following partial output:
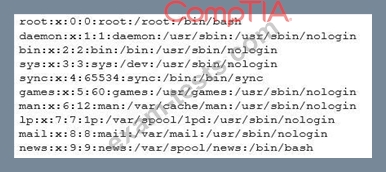
Based on the above output, which of the following should the analyst investigate further?
The analyst uses the command `cat/etc/passwd' and receives the following partial output:

Based on the above output, which of the following should the analyst investigate further?
Question 253
An analyst is reviewing the following log from the company web server:
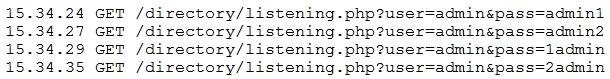
Which of the following is this an example of?

Which of the following is this an example of?
Question 254
A company's Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session. Which of the following is the BEST technique to address the CISO's concerns?
Question 255
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integrating intelligence into hunt operations?

