Question 46
A cybersecurity analyst is reviewing SIEM logs and observes consistent requests originating from an internal host to a blocklisted external server. Which of the following best describes the activity that is
taking place?
taking place?
Question 47
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
Question 48
An analyst is reviewing a vulnerability report for a server environment with the following entries:
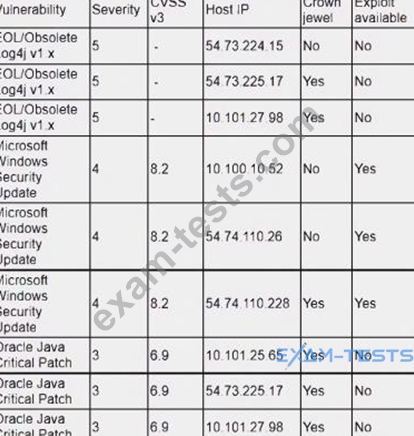
Which of the following systems should be prioritized for patching first?

Which of the following systems should be prioritized for patching first?
Question 49
An analyst is suddenly unable to enrich data from the firewall. However, the other open intelligence feeds continue to work. Which of the following is the most likely reason the firewall feed stopped working?
Question 50
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
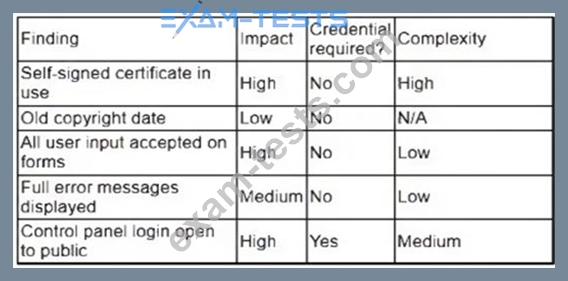
Which of the following should be completed first to remediate the findings?

Which of the following should be completed first to remediate the findings?

