Question 51
An end user forwarded an email with a file attachment to the SOC for review. The SOC analysts think the file was specially crafted for the target. Which of the following investigative actions would best determine if the attachment was malicious?
Question 52
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
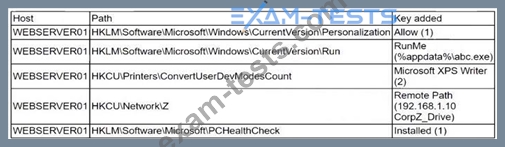
Which of the following best describes the suspicious activity that is occurring?

Which of the following best describes the suspicious activity that is occurring?
Question 53
A security analyst is validating a particular finding that was reported in a web application vulnerability scan to make sure it is not a false positive. The security analyst uses the snippet below:

Which of the following vulnerability types is the security analyst validating?

Which of the following vulnerability types is the security analyst validating?
Question 54
Which of the following best describe the external requirements that are imposed for incident management communication? (Choose two).
Question 55
An MSSP received several alerts from customer 1, which caused a missed incident response deadline for customer 2. Which of the following best describes the document that was violated?

