Question 101
Which of the following types of attacks is most likely to occur after an attacker sets up an evil twin?
Question 102
A user is unable to navigate to a website because the provided URL is not resolving to the correct IP address.
Other users are able to navigate to the intended website without issue. Which of the following is most likely causing this issue?
Other users are able to navigate to the intended website without issue. Which of the following is most likely causing this issue?
Question 103
Users are reporting issues with mobile phone connectivity after a cellular repeater was recently installed.
Users also note that the phones are rapidly losing battery charge. Which of the following should the technician check first to troubleshoot the issue?
Users also note that the phones are rapidly losing battery charge. Which of the following should the technician check first to troubleshoot the issue?
Question 104
A network administrator is planning to host a company application in the cloud, making the application available for all internal and third-party users. Which of the following concepts describes this arrangement?
Question 105
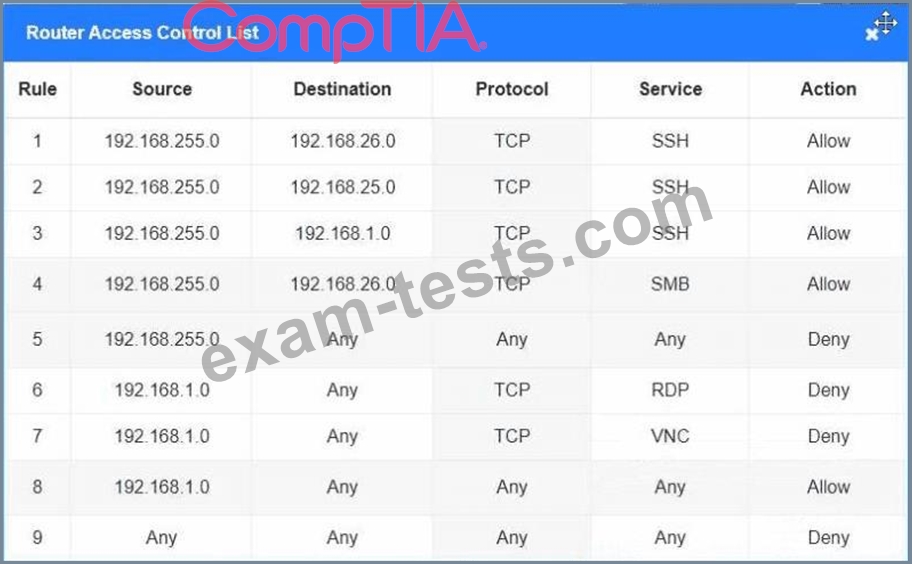
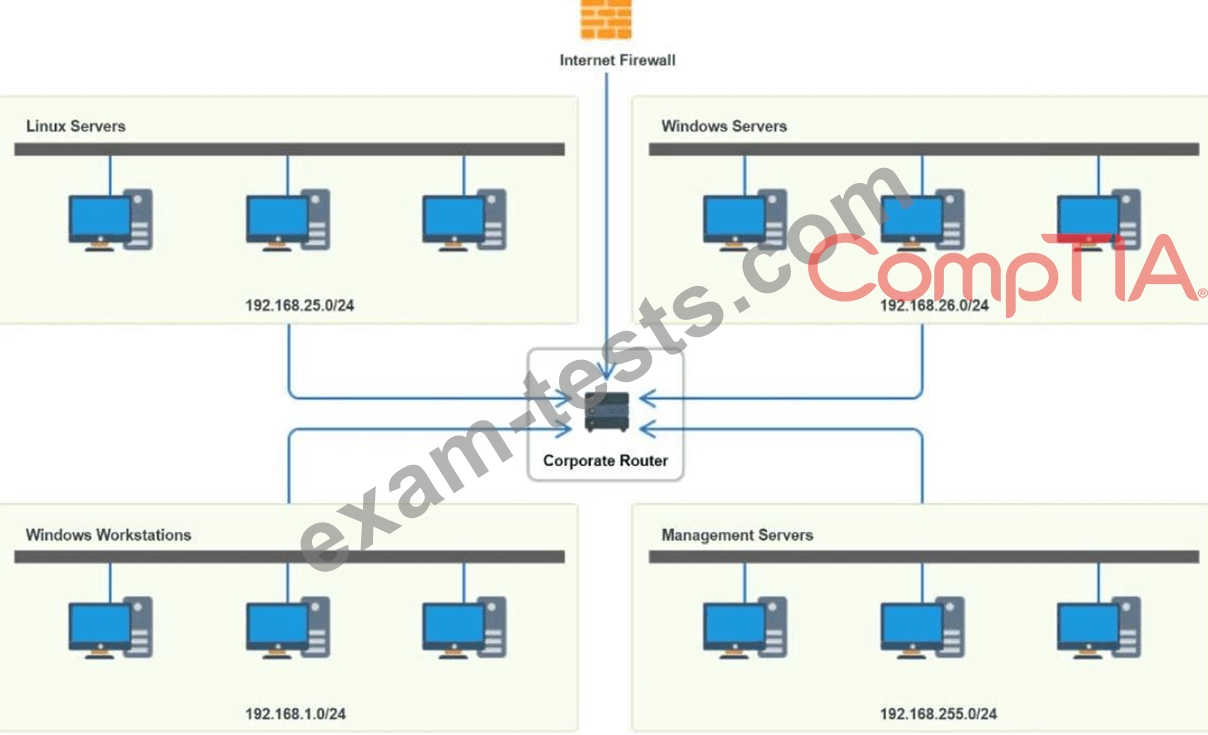
You have been tasked with implementing an ACL on the router that will:
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
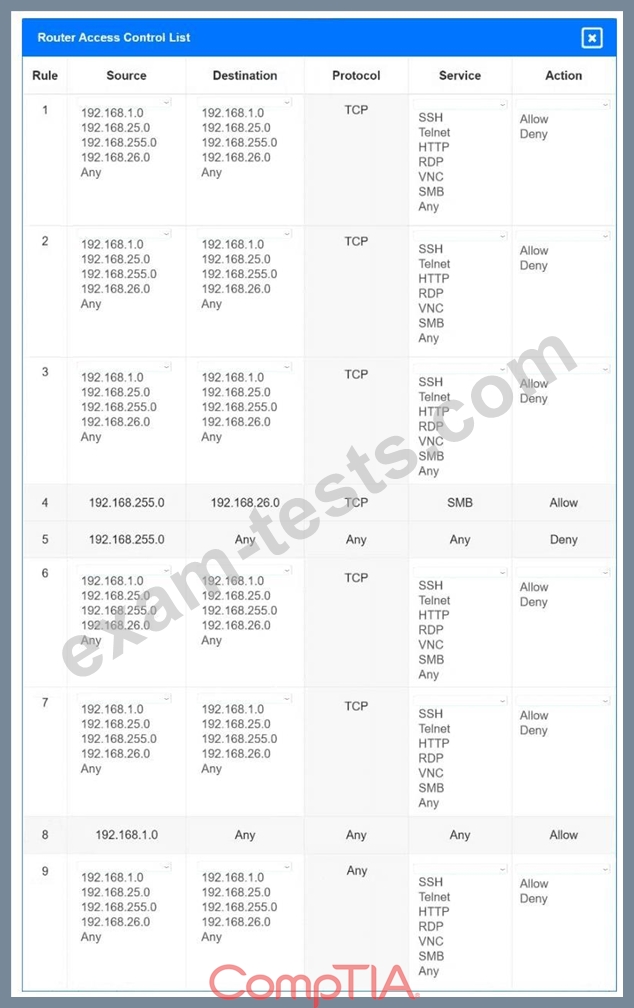
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.