Question 1
While engaging clients for a penetration test from highly regulated industries, which of the following is usually the MOST important to the clients from a business perspective?
Question 2
A MITM attack is being planned. The first step is to get information flowing through a controlled device. Which of the following should be used to accomplish this?
Question 3
A web server is running PHP, and a penetration tester is using LFI to execute commands by passing parameters through the URL. This is possible because server logs were poisoned to execute the PHP system ( ) function. Which of the following would retrieve the contents of the passwd file?
Question 4
A penetration tester runs the following on a machine:
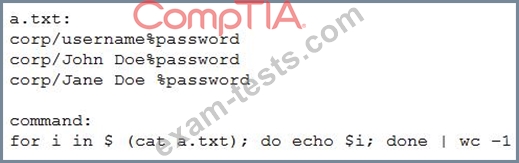
Which of the following will be returned?

Which of the following will be returned?
Question 5
A company requested a penetration tester review the security of an in-house-developed Android application. The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST? (Select TWO)

