Question 36
During the information gathering phase of a network penetration test for the corp.local domain, which of the following commands would provide a list of domain controllers?
Question 37
A penetration tester is checking a script to determine why some basic math errors are persisting. The expected result was the program outputting "True".
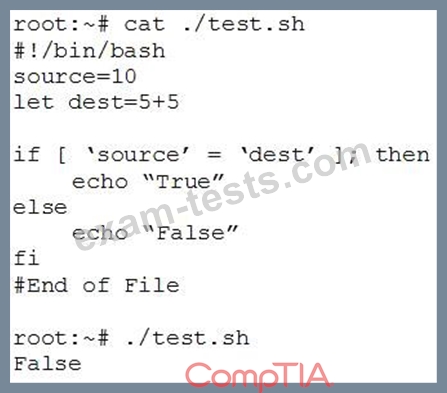
Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)

Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
Question 38
During a vulnerability assessment, the security consultant finds an XP legacy system that is running a criticalmbusiness function.
Which of the following mitigations is BEST for the consultant to conduct?
Which of the following mitigations is BEST for the consultant to conduct?
Question 39
A tester has captured a NetNTLMv2 hash using Responder Which of the following commands will allow the tester to crack the hash using a mask attack?
Question 40
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
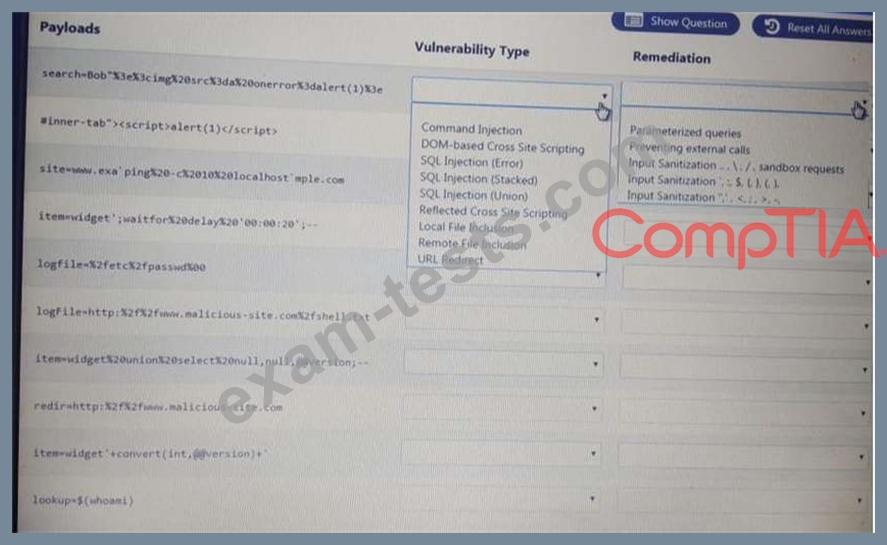

You have been given a list of HTTP payloads that were flagged as malicious.




