Question 31
A penetration tester identifies the following findings during an external vulnerability scan:
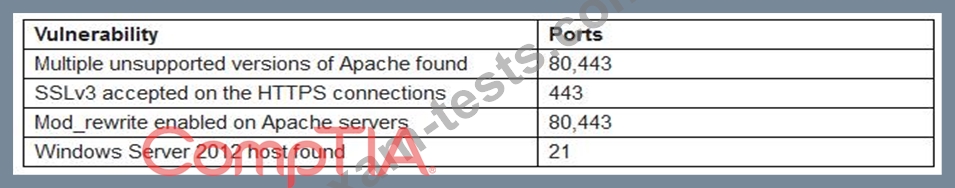
Which of the following attack strategies should be prioritized from the scan results above?

Which of the following attack strategies should be prioritized from the scan results above?
Question 32
Which of the following BEST protects against a rainbow table attack?
Question 33
A client has scheduled a wireless penetration test. Which of the following describes the scoping target information MOST likely needed before testing can begin?
Question 34
A penetration tester wants to script out a way to discover all the RPTR records for a range of IP addresses.
Which of the following is the MOST efficient to utilize?
Which of the following is the MOST efficient to utilize?
Question 35
A penetration tester compromises a system that has unrestricted network over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester mostly like use?

