Question 46
HOTSPOT
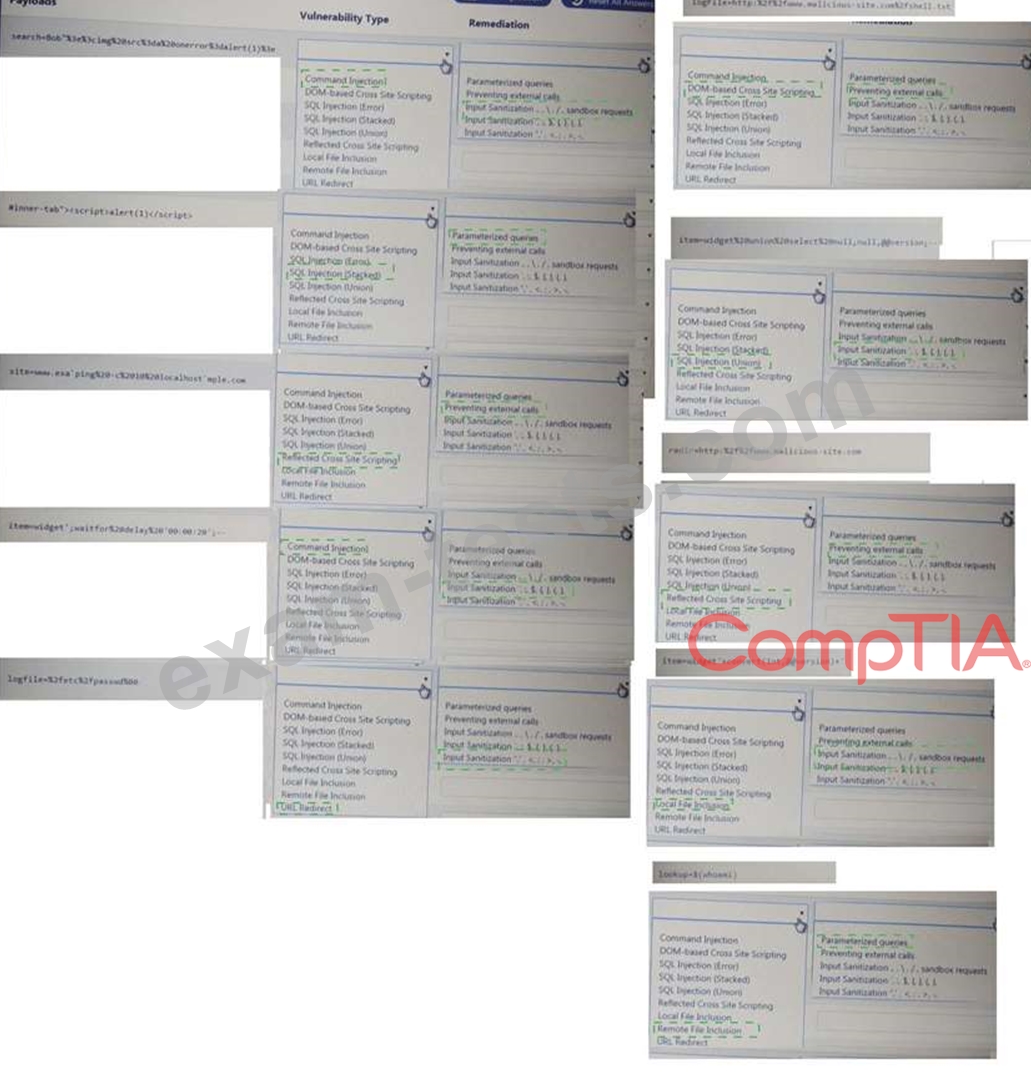
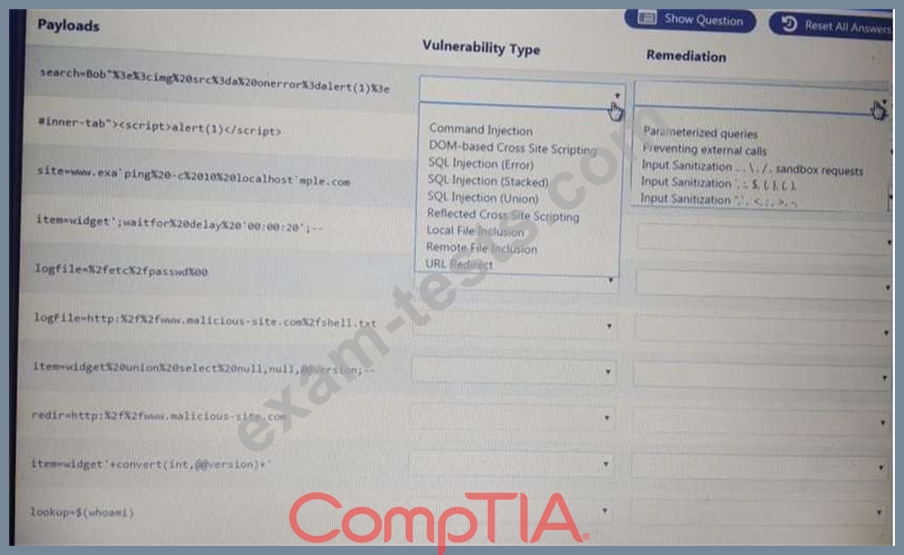
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.

You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.


Question 47
Which of the following tools is used to perform a credential brute force attack?
Question 48
Which of the following is an example of a spear phishing attack?
Question 49
A security assessor completed a comprehensive penetration test of a company and its networks and systems.
During the assessment, the tester identified a vulnerability in the crypto library used for TLS on the company's intranet-wide payroll web application. However, the vulnerability has not yet been patched by the vendor, although a patch is expected within days. Which of the following strategies would BEST mitigate the risk of impact?
During the assessment, the tester identified a vulnerability in the crypto library used for TLS on the company's intranet-wide payroll web application. However, the vulnerability has not yet been patched by the vendor, although a patch is expected within days. Which of the following strategies would BEST mitigate the risk of impact?
Question 50
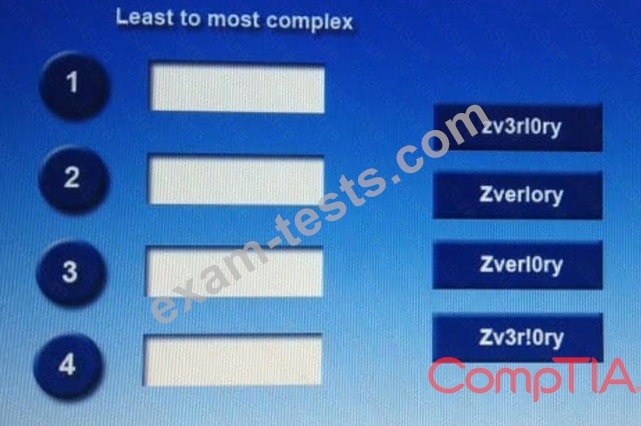
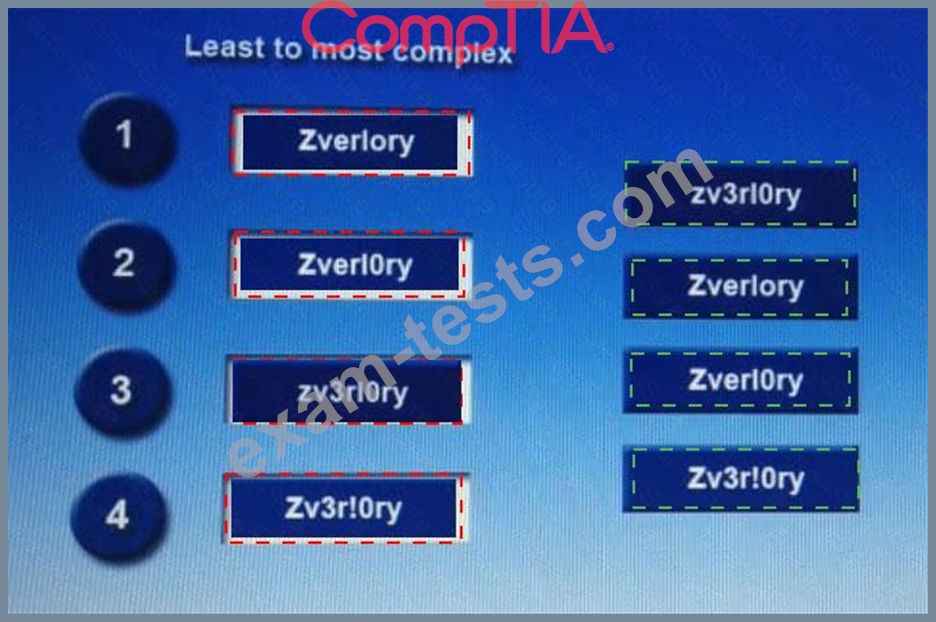
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once