Question 41
A company decides to remediate issues identified from a third-party penetration test done to its infrastructure.
Management should instruct the IT team to:
Management should instruct the IT team to:
Question 42
The following command is run on a Linux file system:
Chmod 4111 /usr/bin/sudo
Which of the following issues may be exploited now?
Chmod 4111 /usr/bin/sudo
Which of the following issues may be exploited now?
Question 43
A tester was able to retrieve domain users' hashes. Which of the following tools can be used to uncover the users' passwords? (Choose two.)
Question 44
An assessor begins an internal security test of the Windows domain internal. comptia. net.
The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A)

B)
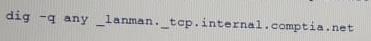
C)
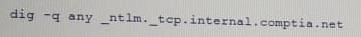
D)

The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A)

B)

C)

D)

Question 45
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below:
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?

