Question 21
A penetration tester has run multiple vulnerability scans against a target system. Which of the following would be unique to a credentialed scan?
Question 22
A client is asking a penetration tester to evaluate a new web application for availability. Which of the following types of attacks should the tester use?
Question 23
Which of the following commands starts the Metasploit database?
Question 24
Which of Ihe following commands would allow a penetration tester to access a private network from the Internet in Metasploit?
Question 25
Given the following Python script:
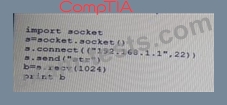
Which of the following actions will it perform?

Which of the following actions will it perform?

