Question 31
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
Question 32
A vulnerability scan report shows what appears to be evidence of a memory disclosure vulnerability on one of the target hosts. The administrator claims the system is patched and the evidence is a false positive.
Which of the following is the BEST method for a tester to confirm the vulnerability exists?
Which of the following is the BEST method for a tester to confirm the vulnerability exists?
Question 33
A company requested a penetration tester review the security of an in-house-developed Android application.
The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST?
(Select TWO)
The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST?
(Select TWO)
Question 34
Instructions:
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
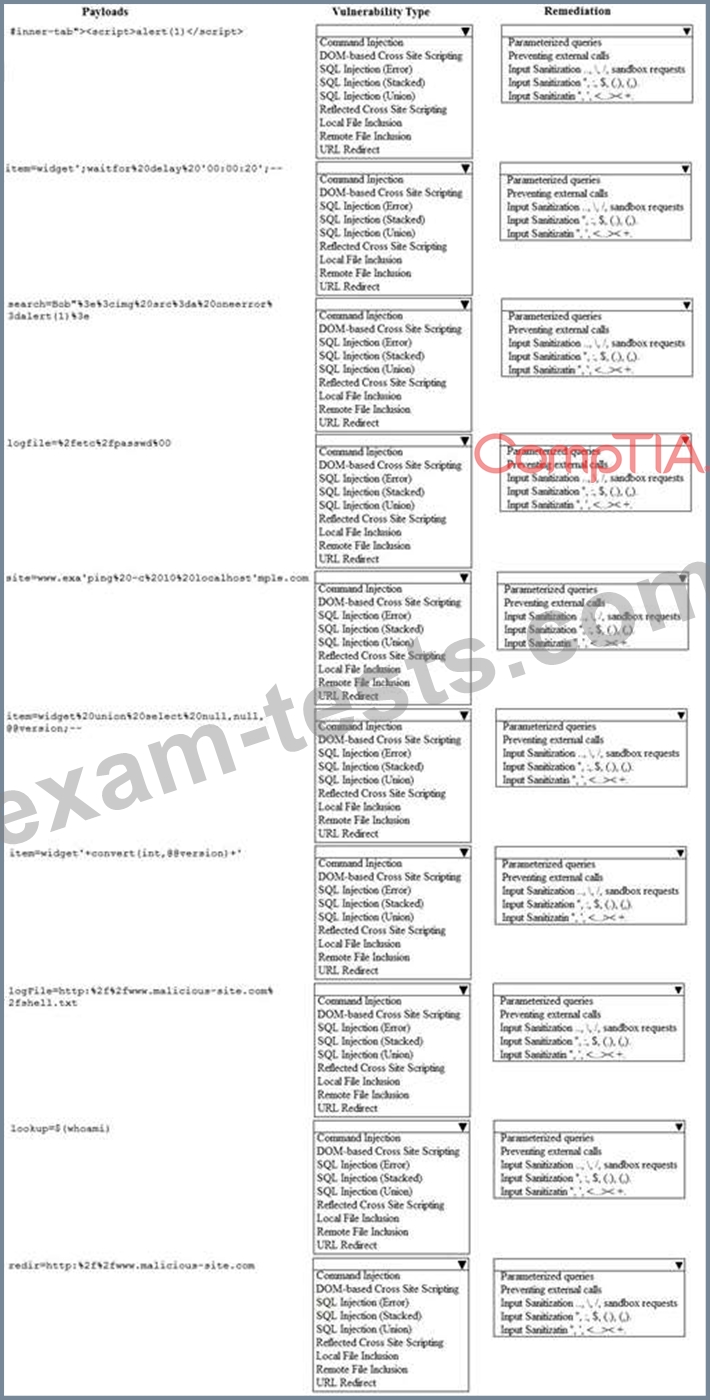
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.

Question 35
A MITM attack is being planned. The first step is to get information flowing through a controlled device. Which of the following should be used to accomplish this?