Question 36
A penetration tester is connected to a client's local network and wants to passively identify cleartext protocols and potentially sensitive data being communicated across the network. Which of the following is the BEST approach to take?
Question 37
Which of the following vulnerabilities are MOST likely to be false positives when reported by an automated scanner on a static HTML web page? (Choose two.)
Question 38
A penetration tester is performing a code review against a web application Given the following URL and source code:
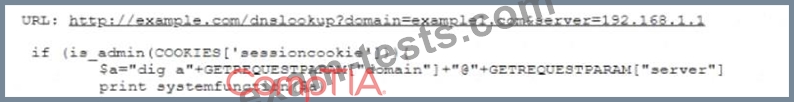
Which of the following vulnerabilities is present in the code above?

Which of the following vulnerabilities is present in the code above?
Question 39
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would define the target list?
Question 40
A client asks a penetration tester to add more addresses to a test currently in progress.
Which of the following would defined the target list?
Which of the following would defined the target list?

