Question 56
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
Question 57
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
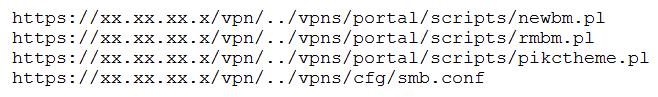
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?

Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
Question 58
A penetration tester wrote the following script to be used in one engagement:
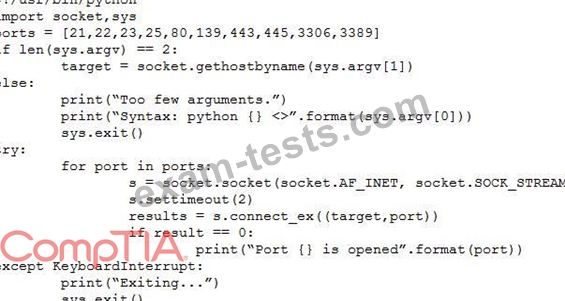
Which of the following actions will this script perform?

Which of the following actions will this script perform?
Question 59
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company's servers. Which of the following actions would BEST enable the tester to perform phishing in a later stage of the assessment?
Question 60
A penetration tester discovers that a web server within the scope of the engagement has already been compromised with a backdoor. Which of the following should the penetration tester do NEXT?

