Question 51
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
Question 52
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format: <name- serial_number>. Which of the following would be the best action for the tester to take NEXT with this information?
Question 53
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
Question 54
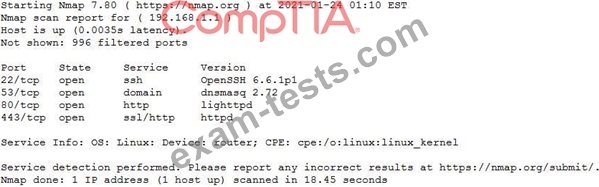
A penetration tester conducts an Nmap scan against a target and receives the following results:

Which of the following should the tester use to redirect the scanning tools using TCP port 1080 on the target?

Which of the following should the tester use to redirect the scanning tools using TCP port 1080 on the target?
Question 55
The results of an Nmap scan are as follows:
Which of the following would be the BEST conclusion about this device?

Which of the following would be the BEST conclusion about this device?

