Question 41
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company's network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
Which of the following actions should the tester take?
Question 42
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client's cybersecurity tools? (Choose two.)
Question 43
Which of the following is the MOST effective person to validate results from a penetration test?
Question 44
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
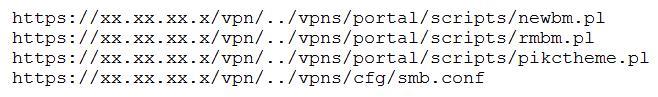
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?

Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
Question 45
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
Premium Bundle
Newest PT0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PT0-002 Exam! BraindumpsPass.com now offer the updated PT0-002 exam dumps, the BraindumpsPass.com PT0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PT0-002 pdf dumps with Exam Engine here:

