Question 26
A penetration tester conducted a discovery scan that generated the following:
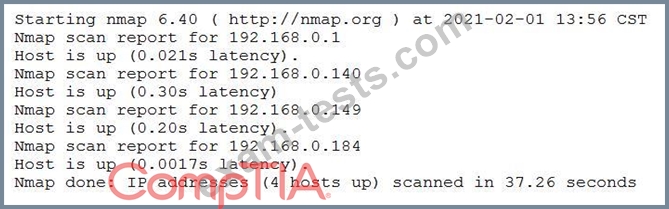
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?

Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
Question 27
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees' phone numbers on the company's website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees' numbers?
In which of the following places should the penetration tester look FIRST for the employees' numbers?
Question 28
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
Question 29
A penetration tester writes the following script:
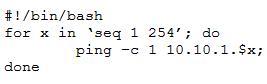
Which of the following objectives is the tester attempting to achieve?

Which of the following objectives is the tester attempting to achieve?
Question 30
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch -r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
cat /dev/null > temp
touch -r .bash_history temp
mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
Premium Bundle
Newest PT0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PT0-002 Exam! BraindumpsPass.com now offer the updated PT0-002 exam dumps, the BraindumpsPass.com PT0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PT0-002 pdf dumps with Exam Engine here:

