Question 31
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
Question 32
A large client wants a penetration tester to scan for devices within its network that are Internet facing. The client is specifically looking for Cisco devices with no authentication requirements. Which of the following settings in Shodan would meet the client's requirements?
Question 33
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
Question 34
A company recruited a penetration tester to configure wireless IDS over the network. Which of the following tools would BEST test the effectiveness of the wireless IDS solutions?
Question 35
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
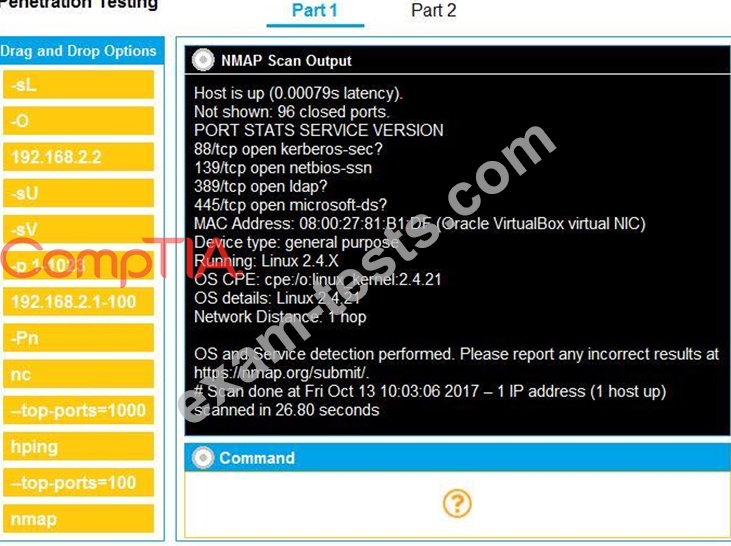
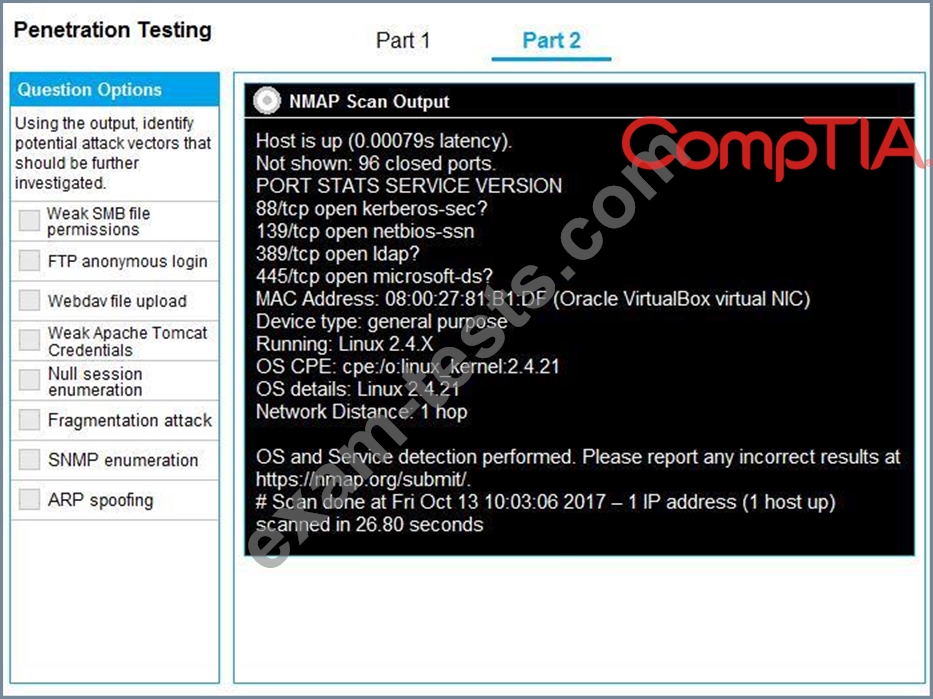
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Premium Bundle
Newest PT0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PT0-002 Exam! BraindumpsPass.com now offer the updated PT0-002 exam dumps, the BraindumpsPass.com PT0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PT0-002 pdf dumps with Exam Engine here:

