Question 51
An engineer is configuring a wireless network using PEAP for the authentication protocol. Which of the following is required?
Question 52
Which of the following encryption methods does PKI typically use to securely protect keys?
Question 53
A security analyst is testing both Windows and Linux systems for unauthorized DNS zone transfers within a LAN on comptia.org from example.org. Which of the following commands should the security analyst use? (Select two.)
Question 54
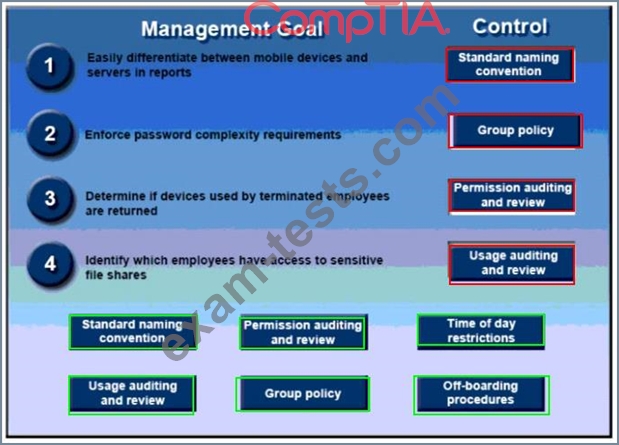
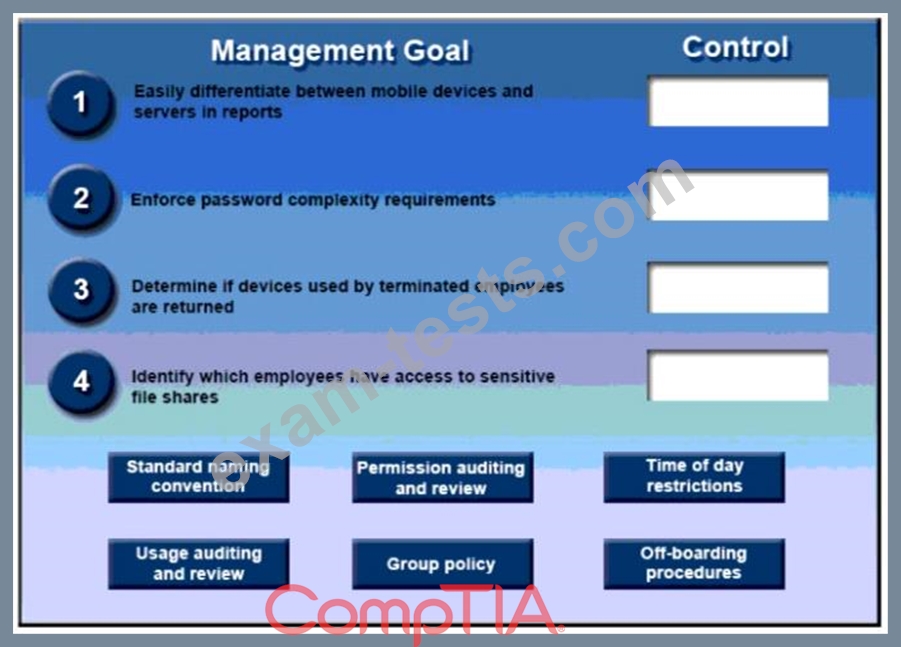
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the appropriate control used to accomplish the account management goal. Options may be used once or not at all.

Question 55
A company is performing an analysis of the corporate enterprise network with the intent of identifying any one system, person, function, or service that, when neutralized, will cause or cascade disproportionate damage to the company's revenue, referrals, and reputation. Which of the following is an element of the BIA that this action is addressing?