Question 61
A security consultant discovers that an organization is using the PCL protocol to print documents, utilizing the default driver and print settings. Which of the following is the MOST likely risk in this situation?
Question 62
A corporation with 35,000 employees replaces its staff laptops every three years. The social responsibility director would like to reduce the organization's carbon footprint and e-waste by donating the old equipment to a charity. Which of the following would be the MOST cost- and time-effective way for the corporation to prevent accidental disclosure of data and minimize additional cost to the charity?
Question 63
A network operations manager has added a second row of server racks in the datacenter. These racks face the opposite direction of the first row of racks.
Which of the following is the reason the manager installed the racks this way?
Which of the following is the reason the manager installed the racks this way?
Question 64
CORRECT TEXT
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls.
Please implement the following requirements:
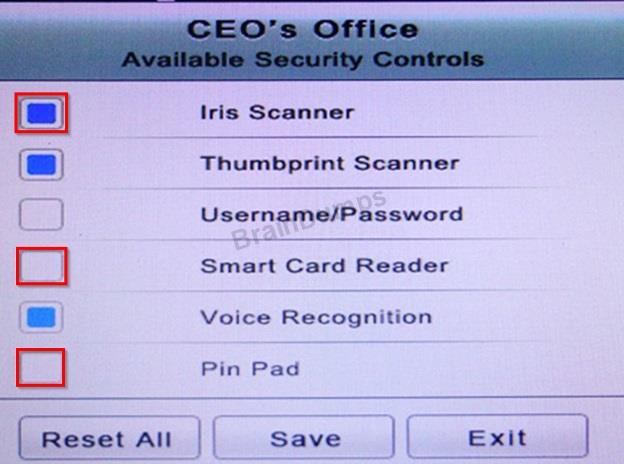
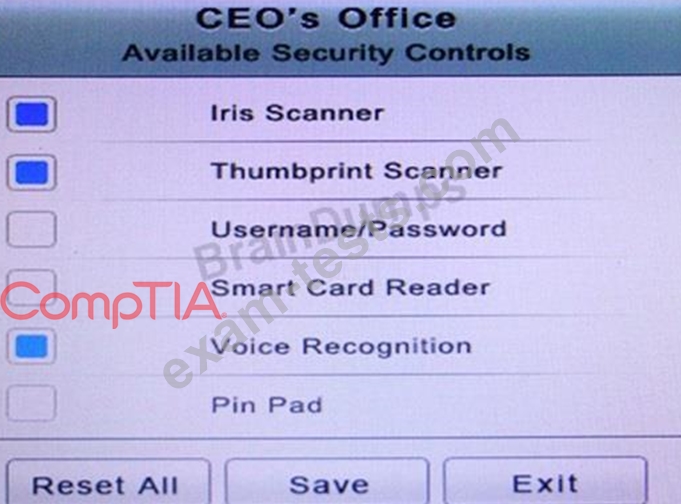
* The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three- factor authentication, while retaining the expensive iris render.
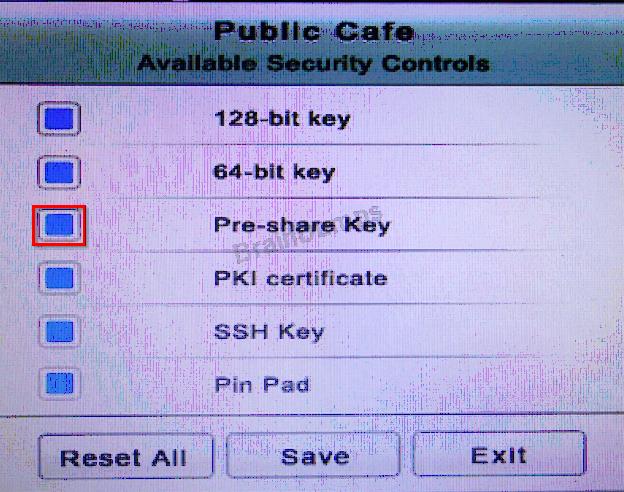
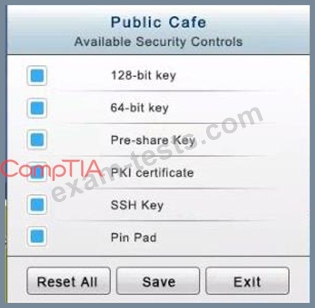
* The Public Cafe has wireless available to customers. You need to secure the WAP with
WPA and place a passphrase on the customer receipts.
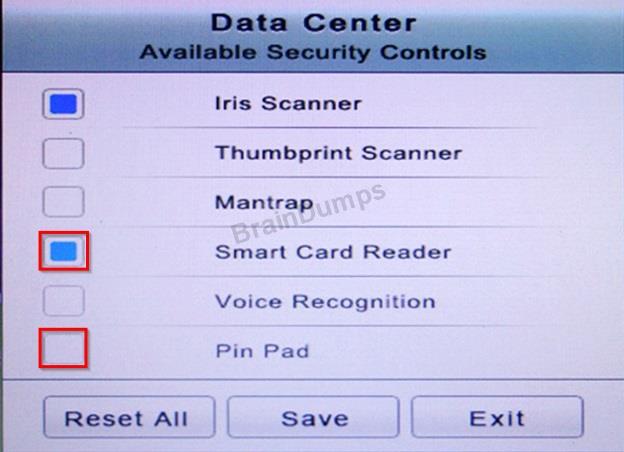
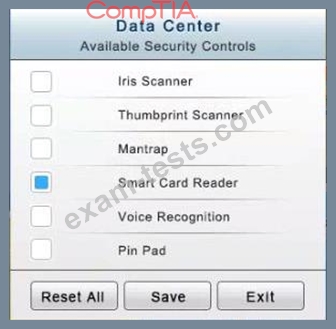
* In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
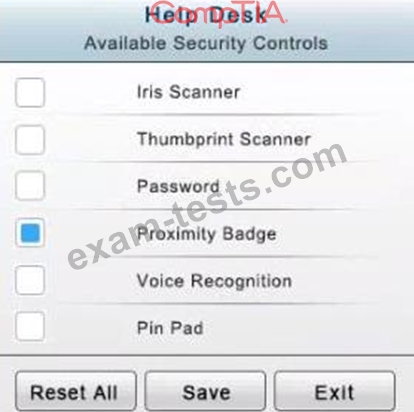
* In the Help Desk Office you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
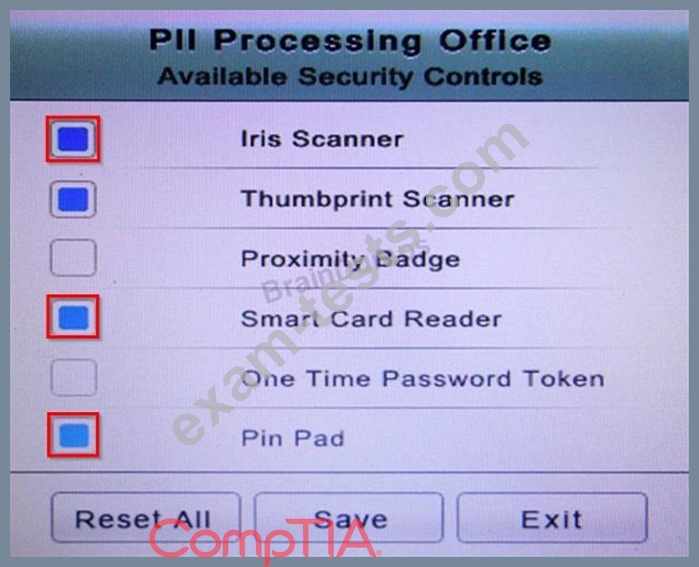
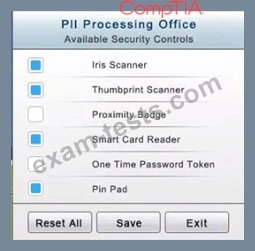
* The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
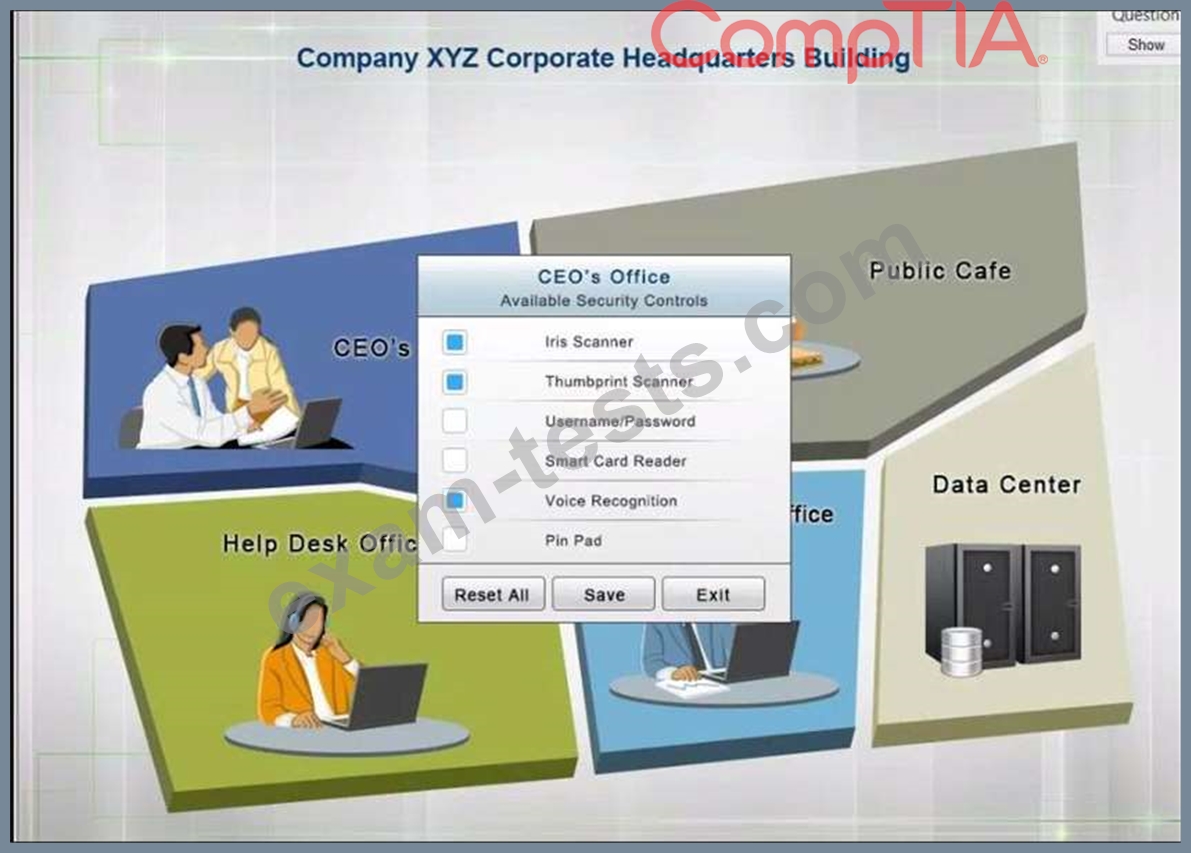
Instructions: The original security controls for each office can be reset at anytime by selecting the Reset button. Once you have met the above requirements for each office, select the Save button.
When you have completed the entire simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls.
Please implement the following requirements:
* The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three- factor authentication, while retaining the expensive iris render.
* The Public Cafe has wireless available to customers. You need to secure the WAP with
WPA and place a passphrase on the customer receipts.
* In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
* In the Help Desk Office you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
* The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.

Instructions: The original security controls for each office can be reset at anytime by selecting the Reset button. Once you have met the above requirements for each office, select the Save button.
When you have completed the entire simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.





Question 65
An organization has hired a new remote workforce. Many new employees are reporting that they are unable to access the shared network resources while traveling. They need to be able to travel to and from different locations on a weekly basis. Shared offices are retained at the headquarters location. The remote workforce will have identical file and system access requirements, and must also be able to log in to the headquarters location remotely. Which of the following BEST represent how the remote employees should have been set up initially?
(Choose two.)
(Choose two.)