Question 71
The firewall administrator is adding a new certificate for the company's remote access solution.
The solution requires that the uploaded file contain the entire certificate chain for the certificate to load properly. The administrator loads the company certificate and the root CA certificate into the file. The file upload is rejected. Which of the following is required to complete the certificate chain?
The solution requires that the uploaded file contain the entire certificate chain for the certificate to load properly. The administrator loads the company certificate and the root CA certificate into the file. The file upload is rejected. Which of the following is required to complete the certificate chain?
Question 72
After a security assessment was performed on the enterprise network, it was discovered that:
1. Configuration changes have been made by users without the consent of IT.
2. Network congestion has increased due to the use of social media.
3. Users are accessing file folders and network shares that are beyond the scope of their need to know.
Which of the following BEST describe the vulnerabilities that exist in this environment? (Choose two.)
1. Configuration changes have been made by users without the consent of IT.
2. Network congestion has increased due to the use of social media.
3. Users are accessing file folders and network shares that are beyond the scope of their need to know.
Which of the following BEST describe the vulnerabilities that exist in this environment? (Choose two.)
Question 73
A company help desk as received several reports that employees have experienced identify theft and compromised accounts. This occurred several days after receiving an email asking them to update their personal bank information. Which of the following is a vulnerability that has been exploited?
Question 74
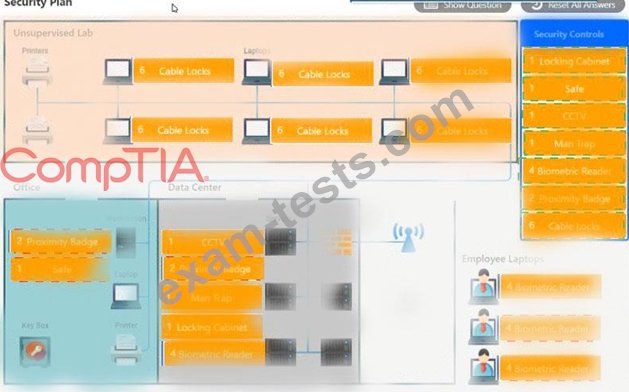
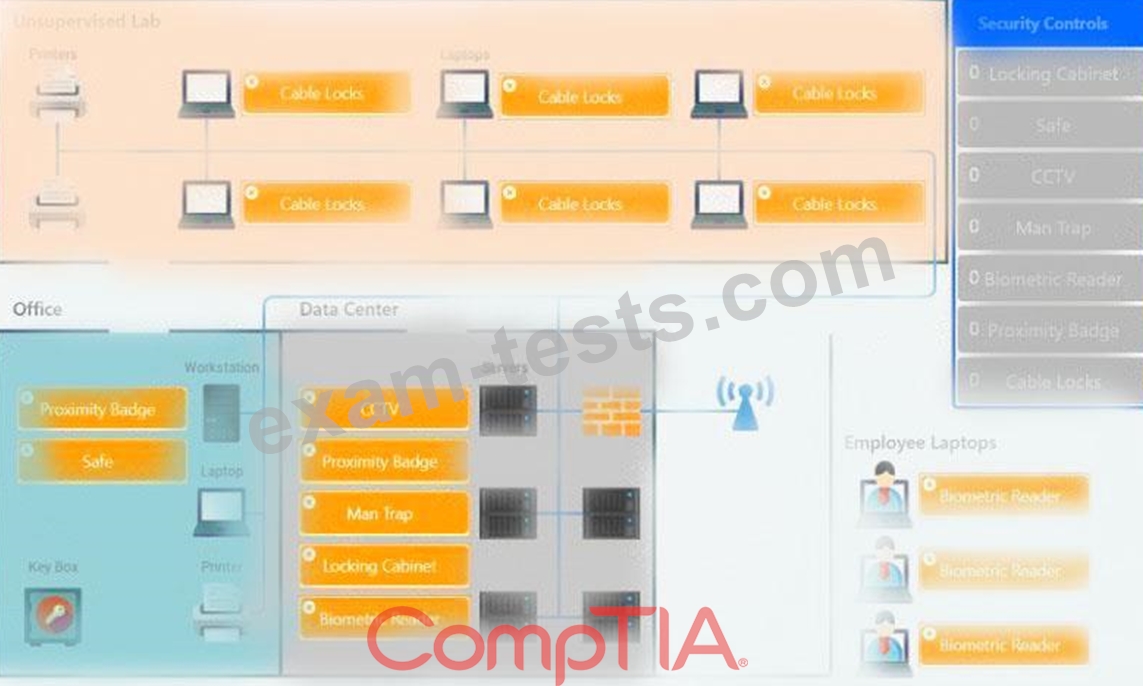
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
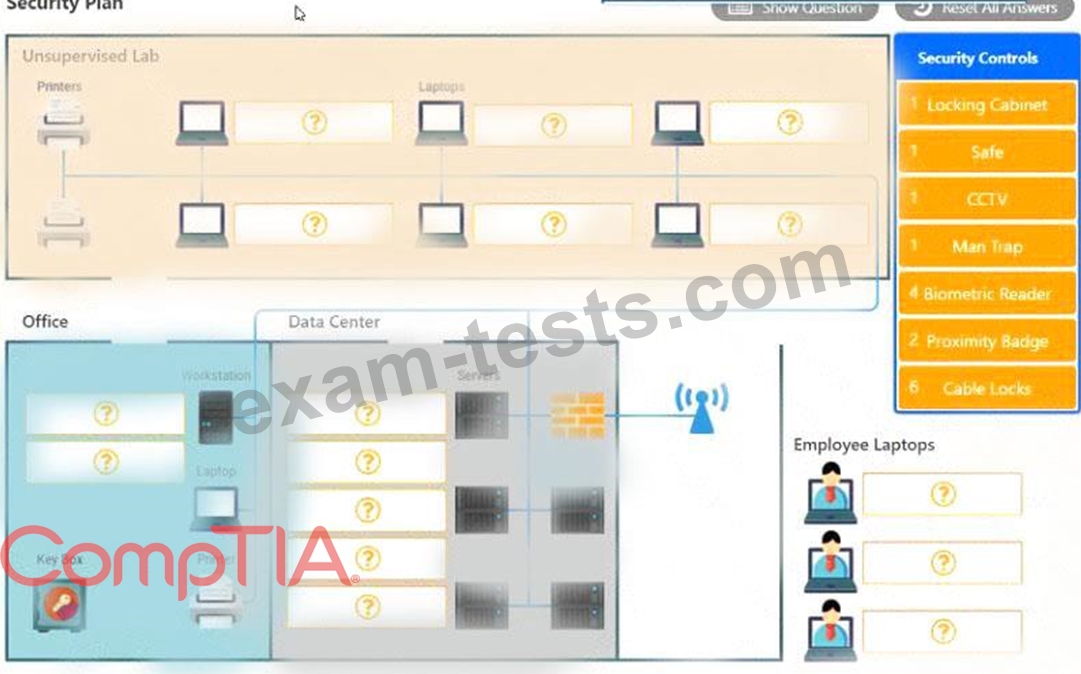
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.

Question 75
A manager wants to distribute a report to several other managers within the company. Some of them reside in remote locations that are not connected to the domain but have a local server. Because there is sensitive data within the report and the size of the report is beyond the limit of the email attachment size, emailing the report is not an option. Which of the following protocols should be implemented to distribute the report securely? (Select three.)