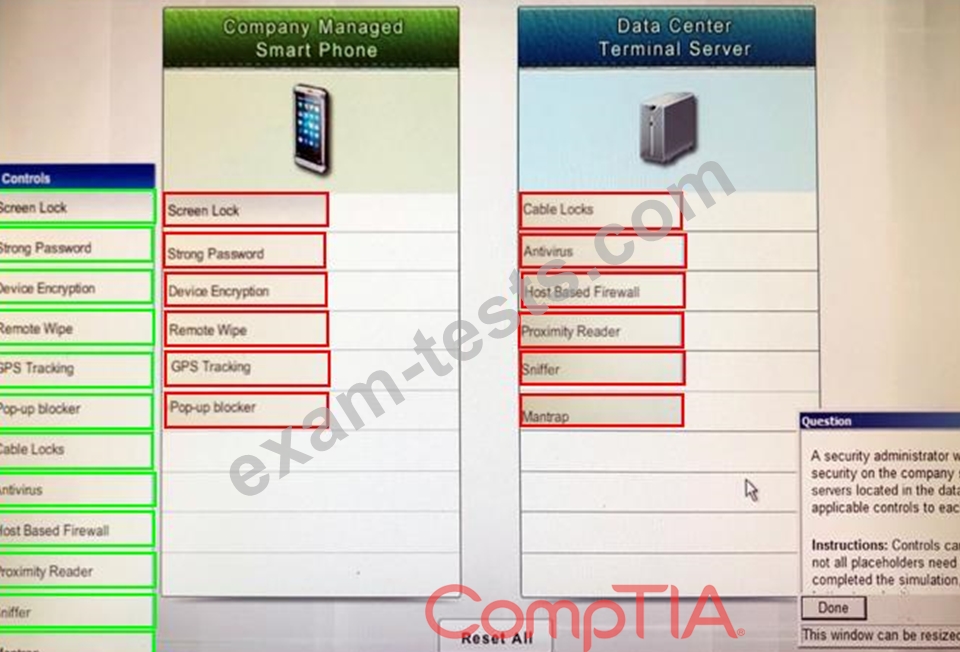
Question 126
A security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and drop the applicable controls to each asset types?
Instructions: Controls can be used multiple times and not all placeholders need to be filled. When you have completed the simulation, please select the Done button to submit.
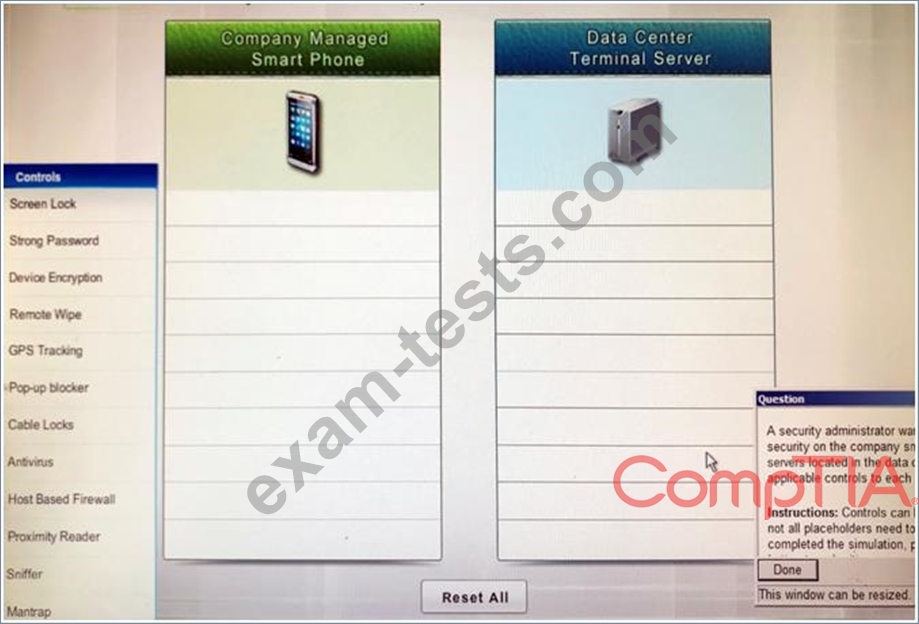
Instructions: Controls can be used multiple times and not all placeholders need to be filled. When you have completed the simulation, please select the Done button to submit.

Question 127
An administrator is beginning an authorized penetration test of a corporate network. Which of the following tools would BEST assist in identifying potential attacks?
Question 128
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message:
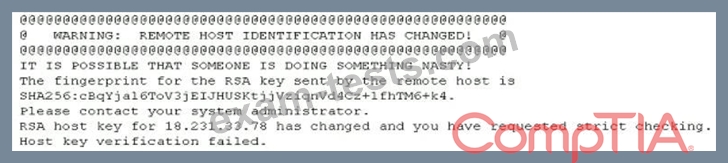
Which of the following network attacks Is the researcher MOST likely experiencing?

Which of the following network attacks Is the researcher MOST likely experiencing?
Question 129
An Organization requires secure configuration baselines for all platforms and technologies that are used. If any system cannot conform to the secure baseline, the organization must process a risk acceptance and receive approval before the system is placed into production. It may have non-conforming systems in its lower environments (development and staging) without risk acceptance, but must receive risk approval before the system is placed in production. Weekly scan reports identify systems that do not conform to any secure baseline.
The application team receive a report with the following results:
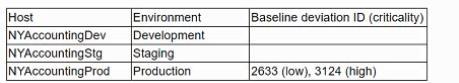
There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take?
The application team receive a report with the following results:

There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take?
Question 130
The Chief information Officer (CIO) has decided to add two-factor authentication along with the use of passwords when logging on to the network. Which of the following should be implemented to BEST accomplish this requirement?