Question 111
A high-security defense installation recently begun utilizing large guard dogs that bark very loudly and excitedly at the slightest provocation. Which of the following types of controls does this BEST describe?
Question 112
A technician, who is managing a secure B2B connection, noticed the connection broke last night. All networking equipment and media are functioning as expected, which leads the technician to Question no certain PKI components. Which of the following should the technician use to validate this assumption? (Choose two.)
Question 113
A security administrator is creating a risk assessment on BYOD. One of the requirements of the risk assessment is to address the following
*Centrally managing mobile devices
*Data loss prevention
Which of the following recommendations should the administrator include in the assessment? (Select TWO).
*Centrally managing mobile devices
*Data loss prevention
Which of the following recommendations should the administrator include in the assessment? (Select TWO).
Question 114
An employee workstation with an IP address of 204 211.38.211/24 reports it is unable to submit print jobs to a network printer at 204.211.38.52/24 after a firewall upgrade. The active firewall rules are as follows:
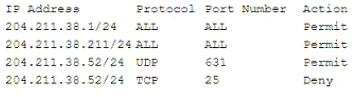
Assuming port numbers have not been changed from their defaults, which of the following should be modified to allow printing to the network printer?

Assuming port numbers have not been changed from their defaults, which of the following should be modified to allow printing to the network printer?
Question 115
A company is allowing a BYOD policy for its staff.
Which of the following is a best practice that can decrease the risk of users jailbreaking mobile devices?
Which of the following is a best practice that can decrease the risk of users jailbreaking mobile devices?

